skimming nfc for credit cards It certainly is. Is it a threat you're likely to face? Realistically, given the "average" threat model, probably not. As RFID technology becomes . See more 1. Turn on near field communication (NFC) Next: 2. Set Google Pay as your default payment app. To use Google Wallet, make sure NFC is enabled and set up correctly on your device. On your Android device, open the Settings app. In .
0 · what is rfid skimming
1 · what is a skimmer
2 · what is a card skimmer
3 · rfid credit card scams
4 · how to identify card skimmer
5 · credit card skimmer checker
6 · card skimmer on checkout machine
7 · card skimmer checker
$5.95
Typically, nefarious actors buy devices that enable them to steal the code produced from your debit/credit card or your smartphone that enables payment. Here's a short video of someone creating an RFID or NFC skimmer: See moreIt certainly is. Is it a threat you're likely to face? Realistically, given the "average" threat model, probably not. As RFID technology becomes . See moreThe obvious answer is to be aware of your surroundings. Generally, this means when using your NFC-enabled smartphone, make sure no weird stranger with an even weirder device in his or her hand is standing too close to you; the same goes for when you use . See more When your credit or debit card information gets skimmed, scammers illegally capture your card details and use them to make unauthorized transactions, create cloned .
NFC/RFID skimming is where hackers/skimmers/bad guys intercept the radio wave communication between devices or simply read the radio waves that a NFC or RFID enabled . When your credit or debit card information gets skimmed, scammers illegally capture your card details and use them to make unauthorized transactions, create cloned .
RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in . Card skimmers record and store credit card information and PINs that can be recovered later to create counterfeit duplicates, which are then used to steal from victims’ .
nadra smart card uses
Skimmers are tiny, malicious card readers hidden within legitimate card readers that harvest data from every person who swipes their cards. After letting the hardware sip data .
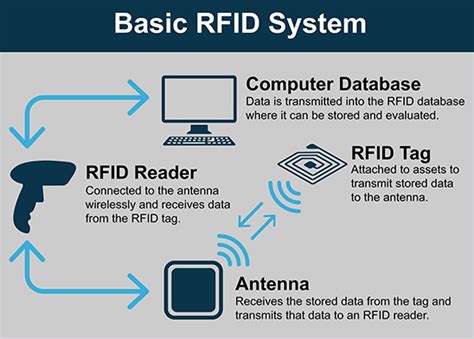
However, as opposed to regular card skimming, NFC communication is encrypted and tokenized – meaning that a card can hardly be duplicated thanks to its information being . Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or . The same size and shape as a credit card, the Hunter Cat detects if a credit card skimmer is trying to steal your data at any given terminal.
You can a credit card with any NFC-equipped phone, but the CV2 code will change with each read, and reusing a code or using codes in the wrong order automatically voids the .
Skimming occurs when devices illegally installed on or inside ATMs, point-of-sale (POS) terminals, or fuel pumps capture card data and record cardholders’ PIN entries. Criminals use .NFC/RFID skimming is where hackers/skimmers/bad guys intercept the radio wave communication between devices or simply read the radio waves that a NFC or RFID enabled . When your credit or debit card information gets skimmed, scammers illegally capture your card details and use them to make unauthorized transactions, create cloned .
RFID skimming is a method to unlawfully obtain someone's payment card information using a RFID reading device. How RFID skimming is performed. Modern payment cards have a built in . Card skimmers record and store credit card information and PINs that can be recovered later to create counterfeit duplicates, which are then used to steal from victims’ . Skimmers are tiny, malicious card readers hidden within legitimate card readers that harvest data from every person who swipes their cards. After letting the hardware sip data .
However, as opposed to regular card skimming, NFC communication is encrypted and tokenized – meaning that a card can hardly be duplicated thanks to its information being .
Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or . The same size and shape as a credit card, the Hunter Cat detects if a credit card skimmer is trying to steal your data at any given terminal.
You can a credit card with any NFC-equipped phone, but the CV2 code will change with each read, and reusing a code or using codes in the wrong order automatically voids the .
what is rfid skimming
national smart card information
what is a skimmer
what is a card skimmer
All that's left is to check that your NFC business card works. Holding the card near a friend's smartphone should be enough to trigger the link to appear, asking if they would like to open the URL in a web browser. From there, they will be able to see your digital . See more
skimming nfc for credit cards|card skimmer checker