can you hijack a smart card authenticated sessions The overall hack can be summarized like this: If I can steal the subject label attached to your authentication method, I might be able to steal your identity even if you use . ZFCARD: Your Professional Polycarbonate ID Card Manufacturer in China. ZFCARD has become one of the leading plastic card and RFID contact identity card manufacturers which we have been doing at our factory since 2008. The .The Nfc Card is a key item within our extensive RFID Card selection.Efficient methods to verify RFID Card suppliers in China involve checking certifications, visiting production facilities, and verifying product samples. Collaborating with a prominent manufacturer ensures quality control .
0 · session hijacking url
1 · session hijacking
2 · ping session hijacking
TimesKey NTAG215 NFC Inkjet Print Cards both sides can be printed compatible with Epson & Canon Inkjet Printers, NOT FOR USE IN PVC CARD PRINTERS and normal thermal ID card printers, Only for use with Inkjet Printers. If you do .
In short: Stealing live sessions enables attackers to bypass authentication controls like MFA. If you can hijack an existing session, you have fewer steps to worry about – no messing about with converting stolen usernames and passwords into an authenticated session. The web server sends the token to the client browser after the client has been authenticated. Through session hijacking, attackers can intercept, predict, or brute-force a . The overall hack can be summarized like this: If I can steal the subject label attached to your authentication method, I might be able to steal your identity even if you use . A session hijacking attack happens when an attacker takes over your internet session — for instance, while you’re checking your credit card balance, paying your bills, or .
session hijacking url
session hijacking
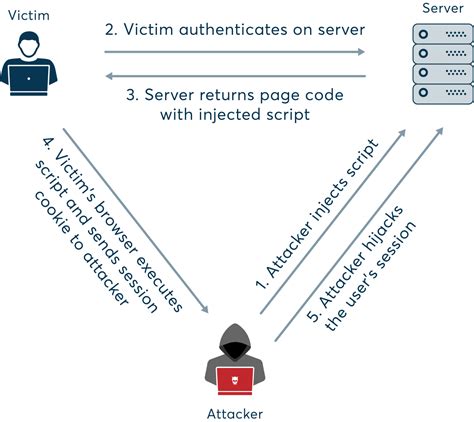
This article will detail the top six techniques for attacking 2FA and present you with an all-around picture for the kind of 2FA attackers you can expect to encounter when working . If the attacker gets that key, they can hijack the authentication process right at the source. This vulnerability has been dubbed the “golden SAML method” because no one has . A cybercriminal can hijack the session of the victim by stealing the session ID or a session cookie to make the server believe that the criminal is the legitimate user. The bad guys can also hijack the session by persuading the .
Man-in-the-middle: Also known as session hijacking or real-time phishing, this attack involves threat actors establishing a fake authentication webpage to trick users into entering .
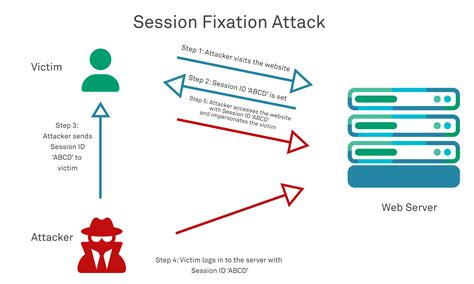
In a session token hijacking attack, the attacker intercepts the session token, allowing them to impersonate the legitimate user. This unauthorized access can lead to significant . In short: Stealing live sessions enables attackers to bypass authentication controls like MFA. If you can hijack an existing session, you have fewer steps to worry about – no messing about with converting stolen usernames and passwords into an authenticated session. The Grand Finale: Hijacking Smart Cards. Smart card redirection also uses the RDPDR channel; it is just another device. This means that if a user connects using a smart card (or just redirects their smart card to use it from within the session), the attacker could also take over the user’s smart card and use it as if it were connected to .
smart card door lock price
ping session hijacking
scr3310v2 smart card reader
The web server sends the token to the client browser after the client has been authenticated. Through session hijacking, attackers can intercept, predict, or brute-force a legitimate session token in order to pose as the authenticated . The overall hack can be summarized like this: If I can steal the subject label attached to your authentication method, I might be able to steal your identity even if you use otherwise very. A session hijacking attack happens when an attacker takes over your internet session — for instance, while you’re checking your credit card balance, paying your bills, or shopping at an online store. Session hijackers usually target browser or web application sessions. This article will detail the top six techniques for attacking 2FA and present you with an all-around picture for the kind of 2FA attackers you can expect to encounter when working as an ethical hacker.
If the attacker gets that key, they can hijack the authentication process right at the source. This vulnerability has been dubbed the “golden SAML method” because no one has yet figured out an effective way to remove this threat.
A cybercriminal can hijack the session of the victim by stealing the session ID or a session cookie to make the server believe that the criminal is the legitimate user. The bad guys can also hijack the session by persuading the victim to log in using a compromised session ID. Man-in-the-middle: Also known as session hijacking or real-time phishing, this attack involves threat actors establishing a fake authentication webpage to trick users into entering their credentials.In a session token hijacking attack, the attacker intercepts the session token, allowing them to impersonate the legitimate user. This unauthorized access can lead to significant consequences, including identity theft and breaches of confidential communications.
In short: Stealing live sessions enables attackers to bypass authentication controls like MFA. If you can hijack an existing session, you have fewer steps to worry about – no messing about with converting stolen usernames and passwords into an authenticated session. The Grand Finale: Hijacking Smart Cards. Smart card redirection also uses the RDPDR channel; it is just another device. This means that if a user connects using a smart card (or just redirects their smart card to use it from within the session), the attacker could also take over the user’s smart card and use it as if it were connected to . The web server sends the token to the client browser after the client has been authenticated. Through session hijacking, attackers can intercept, predict, or brute-force a legitimate session token in order to pose as the authenticated .
The overall hack can be summarized like this: If I can steal the subject label attached to your authentication method, I might be able to steal your identity even if you use otherwise very.
A session hijacking attack happens when an attacker takes over your internet session — for instance, while you’re checking your credit card balance, paying your bills, or shopping at an online store. Session hijackers usually target browser or web application sessions.
This article will detail the top six techniques for attacking 2FA and present you with an all-around picture for the kind of 2FA attackers you can expect to encounter when working as an ethical hacker.
If the attacker gets that key, they can hijack the authentication process right at the source. This vulnerability has been dubbed the “golden SAML method” because no one has yet figured out an effective way to remove this threat. A cybercriminal can hijack the session of the victim by stealing the session ID or a session cookie to make the server believe that the criminal is the legitimate user. The bad guys can also hijack the session by persuading the victim to log in using a compromised session ID. Man-in-the-middle: Also known as session hijacking or real-time phishing, this attack involves threat actors establishing a fake authentication webpage to trick users into entering their credentials.
smart card data storage capacity
The Jakcom R4 is a multifunctional RFID smart ring and a successor to the R3 model. It can .
can you hijack a smart card authenticated sessions|session hijacking url