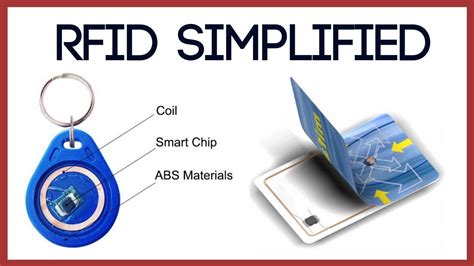
rfid chip security RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See more You can listen to live Auburn Tigers games online or on the radio dial. With 54 stations in the network, the Auburn Sports Network represents one of the biggest and most-listened to college sports network in the South. All home and away .
0 · where are rfid chips used
1 · types of rfid chips
2 · rfid chips in humans
3 · rfid chips for sale
4 · rfid chip pros and cons
5 · rfid chip meaning
6 · rfid chip manufacturing
7 · pros and cons of rfid
(Football) Auburn High vs. North Miami Beach . AU100, Tiger Country 104.5, and SylacaugaNews.com are owned by Marble City Media LLC. Home of Alabama’s 2017 Radio .
RFID chips present currently the best way to protect our ids and passports from counterfeits. If you have a US Passport that is supposed to have an RFID and it does not scan you can pretty much count on being sent to .RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See more
Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See moreRFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more RFID chips present currently the best way to protect our ids and passports from counterfeits. If you have a US Passport that is supposed to have an RFID and it does not scan you can pretty much count on being sent to secondary screening when trying to enter the country, especially if you are traveling from anywhere outside of western europe.Our planned investments will provide the capability for the U.S. to produce one out of every ten memory chips within the next decade. This has profound national security implications, as it ensures a secure supply chain and creates a more reliable, dependable supply of semiconductors.
where are rfid chips used
RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.Implementing robust security practices is crucial for safeguarding RFID systems against potential attacks. Here are some key best practices: Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect sensitive information from unauthorized access.
rfid reader gun diagram
Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming" the. To address the concerns and privacy issues associated with RFID chips, it is crucial to implement appropriate security measures, transparent communication, and robust privacy policies. Encryption, access controls, and data anonymization techniques should be utilized to protect sensitive information. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be wary of these claims; there are better forms of identity theft . Micron is the only company making memory in the U.S. That’s made it a target in the chip war with China, but it’s still building the country’s biggest chip fab.
types of rfid chips
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. RFID chips present currently the best way to protect our ids and passports from counterfeits. If you have a US Passport that is supposed to have an RFID and it does not scan you can pretty much count on being sent to secondary screening when trying to enter the country, especially if you are traveling from anywhere outside of western europe.Our planned investments will provide the capability for the U.S. to produce one out of every ten memory chips within the next decade. This has profound national security implications, as it ensures a secure supply chain and creates a more reliable, dependable supply of semiconductors.
RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
Implementing robust security practices is crucial for safeguarding RFID systems against potential attacks. Here are some key best practices: Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect sensitive information from unauthorized access. Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming" the.
To address the concerns and privacy issues associated with RFID chips, it is crucial to implement appropriate security measures, transparent communication, and robust privacy policies. Encryption, access controls, and data anonymization techniques should be utilized to protect sensitive information.
Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be wary of these claims; there are better forms of identity theft .
Micron is the only company making memory in the U.S. That’s made it a target in the chip war with China, but it’s still building the country’s biggest chip fab.
rfid reader linux usb
rfid chips in humans
rfid reader ic em4095
rfid reader enables
Auburn Tigers. Get live coverage of SEC college football games with home and away feeds for every team on SiriusXM, including the Auburn Tigers. Hear exclusive interviews with Auburn players and coaches, plus expert analysis .Statewide coverage is the hallmark of the Auburn Sports Network's exclusive coverage of Auburn football. All home and away games are broadcast across the entire state .
rfid chip security|rfid chips for sale