smart card based authentication mechanisms Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be . Fans can listen to free, live streaming audio of Auburn Sports Network radio broadcasts of Tiger games and coach's shows. Listen on. Computer; Radio
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
$32.19
Digital authentication against data stored on a smartcard: Smartcards are capable authenticating a person offline with a higher level of assurance.Digital authentication against data stored on a smartcard: Smartcards are capable authenticating a person offline with a higher level of assurance.Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that . Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be .
what is smart card authentication
smart card two factor authentication
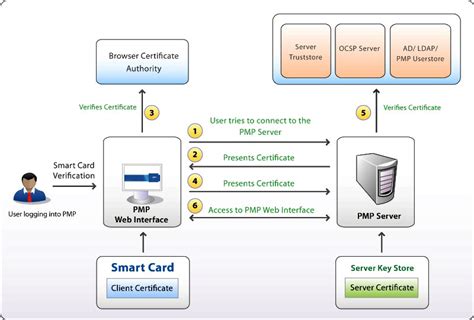
Smart card authentication is a two-step login process that uses a smart card. The smart card stores a user’s public key credentials and a personal identification number (PIN), .Authentication. This inspects, then confirms, the proper identity of people involved in a transaction of data or value. In authentication systems, authentication is measured by assessing the .
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or .
Smart-card-based authentication is one of the most convenient and commonly used authentication mechanisms, as remarked in Ref. 1. It only requires a client to remember .
As the most prevailing two-factor authentication mechanism, smart-card-based password authentication has been a subject of intensive research in the past two decades, .In this paper, we aim to propose a new robust and effective password-based remote user authentication scheme using smart card. Our scheme is efficient, because our scheme uses . Smart-card based password authentication has been the most widely used two-factor authentication (2FA) mechanism for security-critical applications (e.g., e-Health, smart .
Digital authentication against data stored on a smartcard: Smartcards are capable authenticating a person offline with a higher level of assurance.
Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that . Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be . Smart card authentication is a two-step login process that uses a smart card. The smart card stores a user’s public key credentials and a personal identification number (PIN), .Authentication. This inspects, then confirms, the proper identity of people involved in a transaction of data or value. In authentication systems, authentication is measured by assessing the .
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or . Smart-card-based authentication is one of the most convenient and commonly used authentication mechanisms, as remarked in Ref. 1. It only requires a client to remember . As the most prevailing two-factor authentication mechanism, smart-card-based password authentication has been a subject of intensive research in the past two decades, .
smart card certificate authentication
In this paper, we aim to propose a new robust and effective password-based remote user authentication scheme using smart card. Our scheme is efficient, because our scheme uses .
Sep 6, 2022. #2. Try: Signing out your Apple ID on the iPhone. Then use Safari (or any other browser on whatever device) to go to iCloud.com, login with your Apple ID, and go to your .Posted on Nov 1, 2021 12:10 PM. On your iPhone, open the Shortcuts app. Tap on the Automation tab at the bottom of your screen. Tap on Create Personal Automation. Scroll down and select NFC. Tap on Scan. Put .I just bought some NFC tags and my new iphone 12 pro reads them through 3rd party apps but the 'background NFC reader' that the phone is supposed to have doesn't seem to work. I have made sure that I put the tag near the phone when the phone is on, not in airplane .
smart card based authentication mechanisms|configure smart card authentication