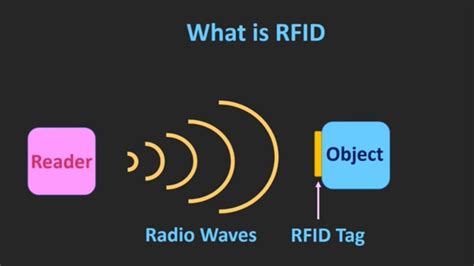
rfid tag 2 factor authentication RFID-enabled identity authentication allows for an effortless, wireless exchange of information between devices. When RFID technology is embedded into a card, smartphone or wearable device, numerous use cases become possible. Nathan King. 22. One of the legends of Auburn's basketball program will no longer be courtside in Neville Arena. Sonny Smith, who coached Auburn to five NCAA Tournaments .
0 · what is rfid verification
1 · rfid verification process
2 · rfid authentication tool
3 · rfid authentication
4 · hid rfid authentication
5 · hid rfid
6 · electronic id rfid
7 · authx rfid
How to listen to Auburn vs. Oklahoma game on radio? The Auburn vs. Oklahoma game will be broadcast live on several radio networks, including KOMA 1520 AM & KRXO 107.7 FM, The Varsity Network and .
Combine RFID credentials with a password for a 2FA solution, or use with other modalities in a full multifactor authentication (MFA) solution. Make passwordless desktop access easy for your users with tap & go login and .
RFID-enabled identity authentication allows for an effortless, wireless exchange of information between devices. When RFID technology is embedded into a card, smartphone or wearable .
Combine RFID credentials with a password for a 2FA solution, or use with other modalities in a full multifactor authentication (MFA) solution. Make passwordless desktop access easy for your users with tap & go login and logout authentication, saving time without sacrificing security.RFID-enabled identity authentication allows for an effortless, wireless exchange of information between devices. When RFID technology is embedded into a card, smartphone or wearable device, numerous use cases become possible. Radio frequency identification (RFID) enables you to read data encoded in RFID chips using specialized equipment—RFID readers. Unlike RFID, near-field communication, or NFC, is a two-way channel for transferring data between devices like phones and smartwatches.Key fobs and multifactor authentication. Key fobs are also used as one of the authentication factors for devices that require two-factor (2FA) or multifactor authentication (MFA). These authentication methods help safeguard a company's network, devices, applications and data.
what is rfid verification
Protect your workforce identities, networks and data with passwordless, phishing-resistant and traditional multi-factor authentication. Talk to an MFA expert.
You can set up the optional 2-factor RFID authentication available on the DL1000V32F and the DL500V32F by following the below instructions : **RFID is available ONLY on DL3FE models provisioned with an RFID chip as of January 1st, 2017**. The DL3/FE device can be paired with up to five RFID tags.This page describes how to configure an RFID badge using Evidians' solution. Authentication Manager is compliant with newest RFID readers. You can authenticate using latest Cherry or NFC readers, among other devices (Hitachi for example).
You can set up the optional 2 factor RFID authentication available on the DL1000V32F and the DL500V32F by following the below instructions : The development of a two-factor RFI and biometric fingerprint authentication-based security scheme is described in this work. It can offer effective control facilities to prevent entry.
rfid verification process
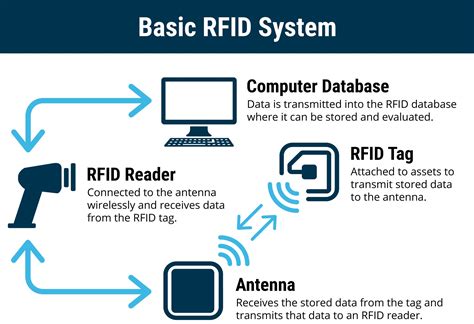
The full authentication process looks like this: The user scans their RFID tag using the RFID & NFC expansion (If you’re unfamiliar with NFC communication, fear not as all is explained in the tutorial). The Omega will send the unique serial number of the scanned tag to a server for verification.
Combine RFID credentials with a password for a 2FA solution, or use with other modalities in a full multifactor authentication (MFA) solution. Make passwordless desktop access easy for your users with tap & go login and logout authentication, saving time without sacrificing security.RFID-enabled identity authentication allows for an effortless, wireless exchange of information between devices. When RFID technology is embedded into a card, smartphone or wearable device, numerous use cases become possible. Radio frequency identification (RFID) enables you to read data encoded in RFID chips using specialized equipment—RFID readers. Unlike RFID, near-field communication, or NFC, is a two-way channel for transferring data between devices like phones and smartwatches.Key fobs and multifactor authentication. Key fobs are also used as one of the authentication factors for devices that require two-factor (2FA) or multifactor authentication (MFA). These authentication methods help safeguard a company's network, devices, applications and data.
rfid authentication tool
Protect your workforce identities, networks and data with passwordless, phishing-resistant and traditional multi-factor authentication. Talk to an MFA expert. You can set up the optional 2-factor RFID authentication available on the DL1000V32F and the DL500V32F by following the below instructions : **RFID is available ONLY on DL3FE models provisioned with an RFID chip as of January 1st, 2017**. The DL3/FE device can be paired with up to five RFID tags.
This page describes how to configure an RFID badge using Evidians' solution. Authentication Manager is compliant with newest RFID readers. You can authenticate using latest Cherry or NFC readers, among other devices (Hitachi for example).You can set up the optional 2 factor RFID authentication available on the DL1000V32F and the DL500V32F by following the below instructions :
The development of a two-factor RFI and biometric fingerprint authentication-based security scheme is described in this work. It can offer effective control facilities to prevent entry.
rfid authentication
hid rfid authentication
hid rfid
View scores and results from week 1 of the 2016 NFL Postseason
rfid tag 2 factor authentication|hid rfid authentication