can mifare card be cloned MIFARE DESFire EV2 credentials cannot be cloned . Even using a supercomputer, it would take 1 billion billion years to crack an AES128-bit key using brute force methods (3). Naturally, cards embedded with this level of security are more expensive than the low frequency alternatives. amal June 18, 2023, 7:26pm 13.
Live coverage of the Texas A&M Aggies vs. Auburn Tigers NCAAF game on ESPN, including live score, highlights and updated stats.
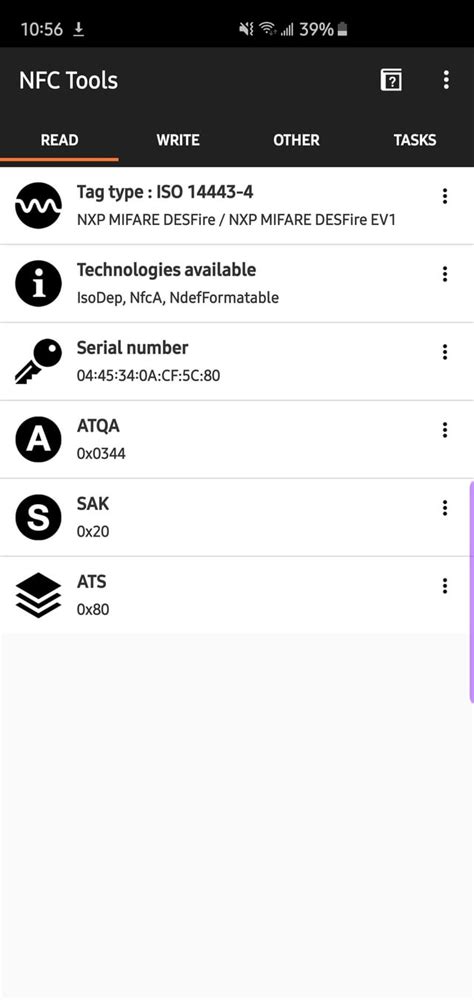
0 · can you clone mifare desfire
1 · can you clone desfire
Listen online to The Tiger 95.9 FM radio station 95.9 MHz FM for free – great choice for Auburn, United States. Listen live The Tiger 95.9 FM radio with Onlineradiobox.com . News/Talk 98.9 WORD: AM 1370 KDTH: 98.5 WNCX: .
can you clone mifare desfire
Depends on the type of MiFare and the depth of your cloning. The encryption of MiFare classic tags has been broken a few years ago, so there is software to crack it for you. If encryption is not used you can copy the contents with freely available Android apps.Long story short, you need to use special chinese "magic" cards to use the mifare .
library rfid detection systems
I tried the exact thing some time ago, purchased a MIFARE card with writable . Depends on the type of MiFare and the depth of your cloning. The encryption of MiFare classic tags has been broken a few years ago, so there is software to crack it for you. If encryption is not used you can copy the contents with freely available Android apps. Here’s how you can clone Mifare NFC Classic 1K Cards using an Android smartphone with NFC capabilities. That’s right. You can use your cell phone to compromise the security of a company if they are using these types of cards.
MIFARE DESFire EV2 credentials cannot be cloned . Even using a supercomputer, it would take 1 billion billion years to crack an AES128-bit key using brute force methods (3). Naturally, cards embedded with this level of security are more expensive than the low frequency alternatives. amal June 18, 2023, 7:26pm 13. Long story short, you need to use special chinese "magic" cards to use the mifare protocol. The mifare protocol works over nfc, but regular generic nfc tags to not adhere to the mifare protocol.
Chose your Mifare classic saved file. At thismpoint app only supports Mifare classic 1k with 4 byte UID. This will write UID and vendor info, with correct checksum. I tried the exact thing some time ago, purchased a MIFARE card with writable sector 0 and tried cloning it with MIFARE classic tool. Did not work, I think it was due to the uni-card being encrypted. The MIFARE classic tool on the Play Store can't bruteforce cards if I remember correctly. Yes it's possible. If the access control system is looking for the UID, Rango NFC can clone the cards, provided if the device is rooted. To do that, hold the card you want to clone at the phone and the app detect the UID and the length. Then click "DO IT!" and the phone will emulate this UID.
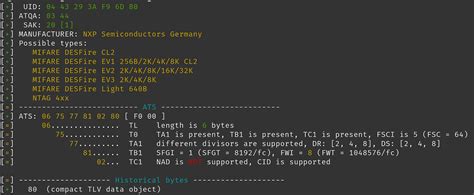
No, as of now, a properly implemented Desfire card system can’t be cloned. The communication between reader and card is encrypted as well, so sniffing it with a Proxmark or others is not possible. The only way to use it is to get it enrolled as a new card. MiFare Ultralight cards typically contain 512 bits (64 bytes) of memory, including 4 bytes (32-bits) of OTP (One Time Programmable) memory where the individual bits can be written but not erased. MiFare Ultralight cards have a 7-byte UID that uniquely identifies the card. The Proxmark 3 RDV4.01 main firmware branches integrate all known MIFARE Classic® cracking techniques, and this episode deep dives into each one. At the end of the video, you'll be familiar with the MIFARE Classic® family of . Depends on the type of MiFare and the depth of your cloning. The encryption of MiFare classic tags has been broken a few years ago, so there is software to crack it for you. If encryption is not used you can copy the contents with freely available Android apps.
Here’s how you can clone Mifare NFC Classic 1K Cards using an Android smartphone with NFC capabilities. That’s right. You can use your cell phone to compromise the security of a company if they are using these types of cards. MIFARE DESFire EV2 credentials cannot be cloned . Even using a supercomputer, it would take 1 billion billion years to crack an AES128-bit key using brute force methods (3). Naturally, cards embedded with this level of security are more expensive than the low frequency alternatives. amal June 18, 2023, 7:26pm 13. Long story short, you need to use special chinese "magic" cards to use the mifare protocol. The mifare protocol works over nfc, but regular generic nfc tags to not adhere to the mifare protocol. Chose your Mifare classic saved file. At thismpoint app only supports Mifare classic 1k with 4 byte UID. This will write UID and vendor info, with correct checksum.
I tried the exact thing some time ago, purchased a MIFARE card with writable sector 0 and tried cloning it with MIFARE classic tool. Did not work, I think it was due to the uni-card being encrypted. The MIFARE classic tool on the Play Store can't bruteforce cards if I remember correctly. Yes it's possible. If the access control system is looking for the UID, Rango NFC can clone the cards, provided if the device is rooted. To do that, hold the card you want to clone at the phone and the app detect the UID and the length. Then click "DO IT!" and the phone will emulate this UID. No, as of now, a properly implemented Desfire card system can’t be cloned. The communication between reader and card is encrypted as well, so sniffing it with a Proxmark or others is not possible. The only way to use it is to get it enrolled as a new card.
MiFare Ultralight cards typically contain 512 bits (64 bytes) of memory, including 4 bytes (32-bits) of OTP (One Time Programmable) memory where the individual bits can be written but not erased. MiFare Ultralight cards have a 7-byte UID that uniquely identifies the card.
can you clone desfire
hybrid rfid systems
Fans can listen to free, live streaming audio of Auburn Sports Network radio .
can mifare card be cloned|can you clone desfire