rfid chip password The T5577 is a chip that can hold data and a configuration (Section 4.12). In the diagram below, all white blocks can hold data. Some can be used for a second purpose, such as the ‘password’ and ‘traceability data’.
If you’re looking for Animal Crossing amiibo bin files, this page has all of our amiibo bin dump links. This is the most commonly used Series 5 amiibo download, and the only trustworthy one I know of. However, since people are .
0 · where are rfid chips used
1 · types of rfid chips
2 · rfid chips in humans
3 · rfid chips for sale
4 · rfid chip pros and cons
5 · rfid chip meaning
6 · rfid chip manufacturing
7 · pros and cons of rfid
The 1998 NFC Wild Card Game was one of the greatest upsets in NFL history and saw the Cardinals win their first playoff game since 1947. (Credit; UPI) This game has to be in the .
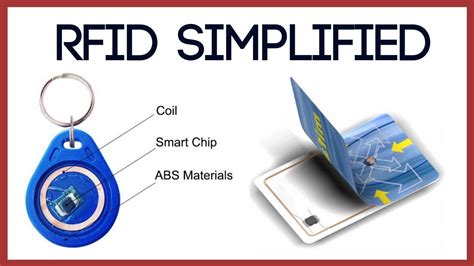
RFID cards can incorporate security features such as encryption, password protection, or authentication protocols. Choose cards that align with your security requirements .How to Choose the Right Chip for Your Needs. Selecting the appropriate ICODE® chip involves evaluating the specific requirements of your application, considering factors such as data .In this video we learn about the T5577 for emulating a variety of LF-RFID tags. We learn how to use the Flipper Zero to clone tags, set & clear passwords. We also learn the technical details.
RFID cards can incorporate security features such as encryption, password protection, or authentication protocols. Choose cards that align with your security requirements to safeguard against unauthorized access or data breaches.How to Choose the Right Chip for Your Needs. Selecting the appropriate ICODE® chip involves evaluating the specific requirements of your application, considering factors such as data security, memory capacity, read range, and operational environment. Here’s a step-by-step guide to help you determine which ICODE® chip best fits your needs. 1. The T5577 is a chip that can hold data and a configuration (Section 4.12). In the diagram below, all white blocks can hold data. Some can be used for a second purpose, such as the ‘password’ and ‘traceability data’.
In certain scenarios, a chip implant can be used as a password replacement for computer login. All of the possible options listed below require a product with an RFID chip that complies with the ISO14443A communication standard. Knowing that, here is a list of encryption options to consider for securing your RFID chip data: Lock Password. This is a 32-bit password that must be transmitted before the tag starts to share data. The 32-bit password has more than 4 million possible combinations.
I’m trying to write to a dual-chip device which is password protected for a purpose with different password, I know the passwords, and removing them is undesired. I just want to be able to specify the password when writing to the device so only the chip with the specified password is written to. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . LOCK PROCEDURE. The steps would be (for a factory default tag): 1. Write a 32 bit (8 hex character) non-zero access password. 2. Lock the selected memory bank. 3. Lock the access password - this will prevent the password from being read or over-written.
where are rfid chips used
1. Decide which memory bank you will be programming your data to. RFID Tags have 4 main memory banks. Only 2 are re-programmable, the EPC and User memory banks. Learn more about all 4 memory banks by reading our article “ 17 Things You Might Not Know About Gen 2 Memory Banks ".In this video we learn about the T5577 for emulating a variety of LF-RFID tags. We learn how to use the Flipper Zero to clone tags, set & clear passwords. We also learn the technical details. RFID cards can incorporate security features such as encryption, password protection, or authentication protocols. Choose cards that align with your security requirements to safeguard against unauthorized access or data breaches.How to Choose the Right Chip for Your Needs. Selecting the appropriate ICODE® chip involves evaluating the specific requirements of your application, considering factors such as data security, memory capacity, read range, and operational environment. Here’s a step-by-step guide to help you determine which ICODE® chip best fits your needs. 1.
The T5577 is a chip that can hold data and a configuration (Section 4.12). In the diagram below, all white blocks can hold data. Some can be used for a second purpose, such as the ‘password’ and ‘traceability data’. In certain scenarios, a chip implant can be used as a password replacement for computer login. All of the possible options listed below require a product with an RFID chip that complies with the ISO14443A communication standard.
Knowing that, here is a list of encryption options to consider for securing your RFID chip data: Lock Password. This is a 32-bit password that must be transmitted before the tag starts to share data. The 32-bit password has more than 4 million possible combinations.
I’m trying to write to a dual-chip device which is password protected for a purpose with different password, I know the passwords, and removing them is undesired. I just want to be able to specify the password when writing to the device so only the chip with the specified password is written to. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . LOCK PROCEDURE. The steps would be (for a factory default tag): 1. Write a 32 bit (8 hex character) non-zero access password. 2. Lock the selected memory bank. 3. Lock the access password - this will prevent the password from being read or over-written.
types of rfid chips
obama rfid chip true or false
neo nazis rfid chip
Get the latest 2024 NFL Playoff Picture seeds and scenarios. See the full NFL conference standings and wild card teams as if the season ended today.
rfid chip password|rfid chip manufacturing