rfid chip purpose In this definition, learn what an operating systems is, how it works and manages all application programs in a computer, and about the types and functions of OSes. They aren't legit cards like you buy in stores, but they work as far as being able to invite villagers to your island. 6. Reply. Mindless-Bluebird420. • 1 yr. ago. I bought three cards from them a .
0 · what does rfid stand for
1 · rfid what does it mean
2 · rfid is involved when using
3 · rfid explained
4 · radio frequency identification tags are
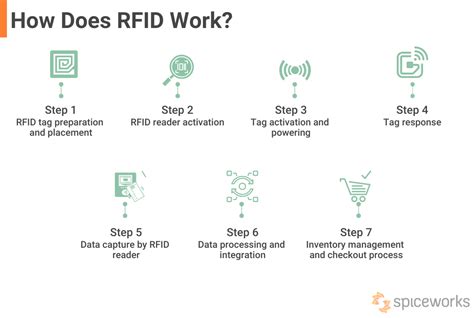
5 · how do rfid work
6 · how do rfid chips work
7 · does 911 use rfids
We only replace items if they are defective or damaged. If you need to exchange it for the same item, send us an email at [email protected] . See more
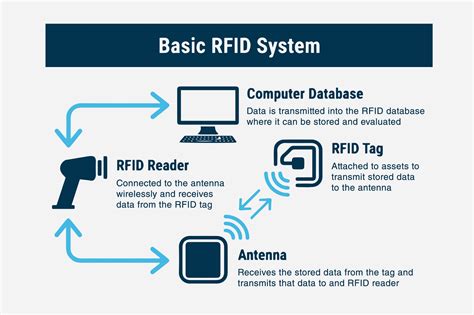
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
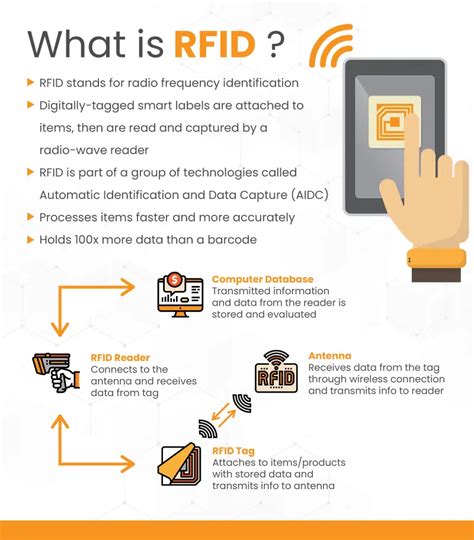
What is the purpose of RFID identification, and what access control problems and security risks are associated with it? RFID stands for radio frequency identification. RFID tags emit radio si.Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods.Information security threats. Mitigating information security threats is an ongoing battle. Here you'll find information on the latest malware and cyberattacks facing enterprises, from viruses and .In this definition, learn what an operating systems is, how it works and manages all application programs in a computer, and about the types and functions of OSes.
User authentication verifies the identity of a user attempting to gain access to a network or computing resource by authorizing a human-to-machine transfer of credentials during interactions on a .Three-factor authentication (3FA) is the use of identity-confirming credentials from three separate categories of authentication factors -- typically, the knowledge, possession and inherence .
Gaining ISO 27002 certification can be a daunting process, so what auditing tools can help? David Mortman weighs in on how to choose the best auditing tool for your organization.advanced persistent threat (APT) An advanced persistent threat (APT) is a prolonged and targeted cyber attack in which an intruder gains access to a network and remains undetected for an extended .
Information security threats. Mitigating information security threats is an ongoing battle. Here you'll find information on the latest malware and cyberattacks facing enterprises, from viruses and .
In this definition, learn what an operating systems is, how it works and manages all application programs in a computer, and about the types and functions of OSes. User authentication verifies the identity of a user attempting to gain access to a network or computing resource by authorizing a human-to-machine transfer of credentials during interactions on a .Three-factor authentication (3FA) is the use of identity-confirming credentials from three separate categories of authentication factors -- typically, the knowledge, possession and inherence .
Gaining ISO 27002 certification can be a daunting process, so what auditing tools can help? David Mortman weighs in on how to choose the best auditing tool for your organization.
what does rfid stand for

what sim card do you put in a smart watch
As your tag already lists the android.nfc.tech.Ndef technology, it is already prepared to store an NDEF message and does not need further formatting. You can simply .
rfid chip purpose|does 911 use rfids