software engineering diagram web app using smart card for authentication Using SCAWA, developers can seamlessly integrate smart-card logon for their web .
The CCID readers below are ideal for MacBooks Pro/Air with Thunderbolt 3/4 or USB-C ports, and the manufacturers provide downloadable drivers for Mac OS. ACS ACR39U-NF fold-away CCID smartcard reader – USB-C. Drivers: PC/SC .Mar 23, 2022. #5. BigBlur said: Apple Pay is basically just an umbrella term for Apple's payment method. It doesn't always mean contactless payment via NFC. There may be an NFC chip, but that still doesn't mean you can do NFC/contactless stuff. This article says there is a NFC .
0 · how to design authentication systems
1 · digital authentication system design
2 · authentication system design examples
3 · authentication system case diagram
4 · authentication methods for web applications
5 · authentication for web application
6 · authentication design software
These are our NFC Intent filters nfcAdapter.ACTION_TAG_DISCOVERED — NFC tag discovered. .
how to design authentication systems
tag rfid para vehiculos
digital authentication system design
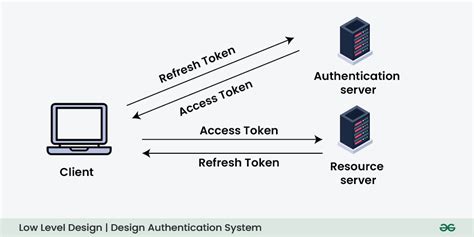
Use Case Diagram for Authentication System Design. The web user initiates the interaction by logging in or registering. After successful authentication, the user can perform actions like viewing transaction history, . app authentication involves several methods, including cookies, JWT, OAuth, API Token, SAML, and OpenID. Depending on the use case and the security requirements, they have various advantages and . Gain stakeholder alignment on the web application software development and implementation plan. 5 steps to create a architecture diagram for a web application
This article focuses on a best practice model grounded in JWT (JSON Token) based architecture, a prevalent choice for user authentication in modern systems.Fig. 1 shows a typical authentication process—in this case, a single sign-on (SSO) that allows .Using SCAWA, developers can seamlessly integrate smart-card logon for their web .

We present an extension of this repository in the form of a highly requested new authentication .It defines a Java API for communication with Smart Cards using ISO/IEC 7816-4 APDUs. It .
thingmagic uhf usb rfid reader development kit
This UML sequence template can help you: - Show the sequence of events involved in the web application authentication process. - Save time by auto-generating your sequence diagram. - Easily create and edit your sequence . Use Case Diagram for Authentication System Design. The web user initiates the interaction by logging in or registering. After successful authentication, the user can perform actions like viewing transaction history, checking balance, or processing bill payments. app authentication involves several methods, including cookies, JWT, OAuth, API Token, SAML, and OpenID. Depending on the use case and the security requirements, they have various advantages and downsides. Gain stakeholder alignment on the web application software development and implementation plan. 5 steps to create a architecture diagram for a web application

This article focuses on a best practice model grounded in JWT (JSON Token) based architecture, a prevalent choice for user authentication in modern systems.Fig. 1 shows a typical authentication process—in this case, a single sign-on (SSO) that allows a user to access multiple applications with one set of login credentials. This SSO is modeled using a UML activity diagram. With an SSO, a client accesses multiple resources connected to a local area network [13].Using SCAWA, developers can seamlessly integrate smart-card logon for their web applications, by only implementing a usual OAuth 2.0 flow. Through this contribution, we aim to lower the entry barrier for implementing sophisticated and secure authentication and authorization methods.
We present an extension of this repository in the form of a highly requested new authentication token validation library for PHP language, a Nextcloud application enabling -eID 2-factor authentication, and a new JavaCard applet fully compatible with the -eID solution.
It defines a Java API for communication with Smart Cards using ISO/IEC 7816-4 APDUs. It thereby allows Java applications to interact with applications running on the Smart Card, to store and retrieve data on the card, etc.
This UML sequence template can help you: - Show the sequence of events involved in the web application authentication process. - Save time by auto-generating your sequence diagram. - Easily create and edit your sequence diagram.
Technical overview of authentication and digital signing. The authentication and digital signing processes share a common scheme – the eID application signs a server-sent datagram with the private key on the smart card and sends the certificate and signature cryptogram back to .
Use Case Diagram for Authentication System Design. The web user initiates the interaction by logging in or registering. After successful authentication, the user can perform actions like viewing transaction history, checking balance, or processing bill payments. app authentication involves several methods, including cookies, JWT, OAuth, API Token, SAML, and OpenID. Depending on the use case and the security requirements, they have various advantages and downsides. Gain stakeholder alignment on the web application software development and implementation plan. 5 steps to create a architecture diagram for a web application This article focuses on a best practice model grounded in JWT (JSON Token) based architecture, a prevalent choice for user authentication in modern systems.
Fig. 1 shows a typical authentication process—in this case, a single sign-on (SSO) that allows a user to access multiple applications with one set of login credentials. This SSO is modeled using a UML activity diagram. With an SSO, a client accesses multiple resources connected to a local area network [13].
Using SCAWA, developers can seamlessly integrate smart-card logon for their web applications, by only implementing a usual OAuth 2.0 flow. Through this contribution, we aim to lower the entry barrier for implementing sophisticated and secure authentication and authorization methods.We present an extension of this repository in the form of a highly requested new authentication token validation library for PHP language, a Nextcloud application enabling -eID 2-factor authentication, and a new JavaCard applet fully compatible with the -eID solution.It defines a Java API for communication with Smart Cards using ISO/IEC 7816-4 APDUs. It thereby allows Java applications to interact with applications running on the Smart Card, to store and retrieve data on the card, etc.
This UML sequence template can help you: - Show the sequence of events involved in the web application authentication process. - Save time by auto-generating your sequence diagram. - Easily create and edit your sequence diagram.
To begin with, head over to Settings > Apps > All Apps. Then select Google Pay from the list and go to Storage. Now tap on Clear Storage > OK in the confirmation dialog box. Likewise, delete the data for Google Play .A black USB connected desktop NFC device which supports reading/writing NFC tags, peer-to .
software engineering diagram web app using smart card for authentication|authentication system case diagram