rfid tag security system RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials. UNF ID. Where do we go to get our ID card? There’s an office in between the Chick-Fil-A and .
0 · types of rfid systems
1 · rfid systems for manufacturing
2 · rfid reader for gate access
3 · rfid gate entry systems
4 · rfid gate access control system
5 · rfid based door access control
6 · best rfid for access control
7 · are rfid tags reusable
Game / TV; 4:30 pm: NFC Wild Card Game. Packers vs Cowboys. FOX. 8:15 pm: NFC Wild Card Game. Rams vs Lions. NBC, Peacock. Monday, January 15, 2024. . was only for two years. From here on, the split of the six-game Wild .
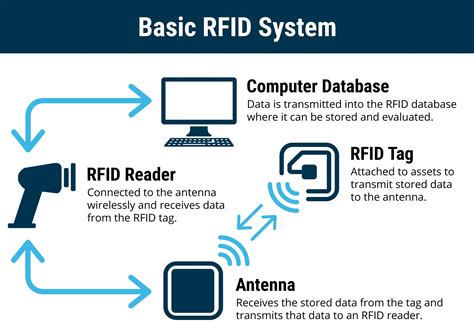
An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. The system achieves contactless access control by identifying users carrying RFID tags and is .An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. The system achieves contactless access control by identifying users carrying RFID tags and is widely used in enterprises, schools, hospitals, and other locations.RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials. RFID access control refers to systems that use RFID technology to allow or deny access to a particular area or facility. The system uses RFID key cards or tags, which carry embedded microchips that communicate wirelessly with RFID readers installed at multiple access points, such as doors or gates, to manage access.
Tags: RFID tags are the cornerstone of the system, serving as the identifiers for assets. These compact devices consist of an integrated circuit or microchip that stores unique identification data and an antenna for communication. Tags come in . This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. RFID (Radio Frequency Identification) Systems are wireless communication systems that use radio waves to identify, categorize, and track objects, people, or animals by attaching RFID tags to them, which can be read by RFID readers without requiring line-of . 1. Avigilon emerges as a frontrunner in RFID access control systems, offering a comprehensive solution that integrates seamlessly with existing security networks. This system is designed for high-security environments where precise control over access permissions is paramount. Key Features: High-definition RFID readers for accurate identification.
RFID tags are small, electronic devices that store and transmit information. These tags can be attached to various objects, including products, assets, and even animals. When an RFID reader sends out a signal, the RFID tag responds with its stored data, allowing for quick and efficient identification and tracking. Benefits of RFID Technology. 1. Skimming: To skim is to surreptitiously read a tag, often through the use of a handheld reader. If your system is configured according to a widely used protocol, it may be at risk of being skimmed. 2. RFID security tags are the simplest way for your business to keep track of inventory, shipments, and protect against theft. Small, inexpensive, and effective, if you don’t currently use them then you need to seriously reconsider! This article will explain what they are, how they work, and where they can be used.An RFID access control system is a security management system based on radio frequency identification technology, designed to control and manage personnel access to specific areas. The system achieves contactless access control by identifying users carrying RFID tags and is widely used in enterprises, schools, hospitals, and other locations.
RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials. RFID access control refers to systems that use RFID technology to allow or deny access to a particular area or facility. The system uses RFID key cards or tags, which carry embedded microchips that communicate wirelessly with RFID readers installed at multiple access points, such as doors or gates, to manage access.Tags: RFID tags are the cornerstone of the system, serving as the identifiers for assets. These compact devices consist of an integrated circuit or microchip that stores unique identification data and an antenna for communication. Tags come in .
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
types of rfid systems
RFID (Radio Frequency Identification) Systems are wireless communication systems that use radio waves to identify, categorize, and track objects, people, or animals by attaching RFID tags to them, which can be read by RFID readers without requiring line-of . 1. Avigilon emerges as a frontrunner in RFID access control systems, offering a comprehensive solution that integrates seamlessly with existing security networks. This system is designed for high-security environments where precise control over access permissions is paramount. Key Features: High-definition RFID readers for accurate identification.RFID tags are small, electronic devices that store and transmit information. These tags can be attached to various objects, including products, assets, and even animals. When an RFID reader sends out a signal, the RFID tag responds with its stored data, allowing for quick and efficient identification and tracking. Benefits of RFID Technology.
1. Skimming: To skim is to surreptitiously read a tag, often through the use of a handheld reader. If your system is configured according to a widely used protocol, it may be at risk of being skimmed. 2.
rfid systems for manufacturing
rfid reader for gate access
rfid gate entry systems
$16.99
rfid tag security system|rfid based door access control