relay attack on smart card fully executed a relay attack against an ISO 14443A contactless smart card, up to a distance of 50 m. Simply relaying information between the card and reader over a longer distance does not . Have a look at the number 14 in the footnotes at the bottom of this link: iOS 14 - Apple. With that said, if the NFC tag isn't scanning automatically when using the associated .
0 · relay attack meaning
1 · how do relay attacks work
2 · example of a relay attack
3 · car relay attack examples
Short answer, No. Long answer Opal cards do not work on mobile devices as payment cards .Fund open source developers The ReadME Project. GitHub community articles Repositories. . android nfc-card-reader octopus android-nfc nfc-reader octopus-card hkoctopus Updated Aug 1, 2022; . Add this topic to your repo To associate your repository with the .
relay attack meaning
A relay attack is a cyber-attack that intercepts and relays communication between two devices to gain unauthorized access. Learn how relay attacks work, see real-life examples, and discover .
how do relay attacks work
fully executed a relay attack against an ISO 14443A contactless smart card, up to a distance of 50 m. Simply relaying information between the card and reader over a longer distance does not . A relay attack is a type of interception attack that relays information between two parties without their consent or knowledge. Learn how relay attacks work, how they differ from MITM and replay attacks, and how to prevent them with examples from car theft, SMB, and contactless card scenarios.
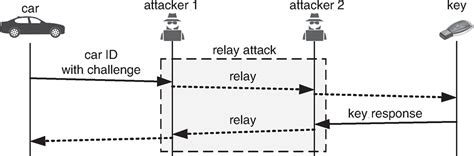
A relay attack is a cyber-attack that intercepts and relays communication between two devices to gain unauthorized access. Learn how relay attacks work, see real-life examples, and discover how to protect against them with Twingate.fully executed a relay attack against an ISO 14443A contactless smart card, up to a distance of 50 m. Simply relaying information between the card and reader over a longer distance does not require the same techni-cal resources from the attacker as hardware tampering or cryptanalysis.An attacker can use a proxy-token and proxy-reader to relay the communication between a legitimate reader and token over a greater distance than intended, thereby tricking the reader into believing that the real token is in close proximity.
Learn how relay attacks exploit the communication between legitimate parties and how distance-bounding schemes can prevent them. This chapter covers the concept, mechanisms, and challenges of distance bounding in security of ubiquitous computing systems.
Relay attack against a contactless smart card. The concept of relay attack was introduced in the “Grandmaster Chess Attack” scenario [6] . An attacker can win a chess match against a grandmaster without even knowing the rules of the game.A relay attack is a hacking technique that relays messages between two parties without manipulating them. It can be used to break into a high-security building with a smart card, for example.
example of a relay attack
car relay attack examples
auburn baseball online radio
The relay attack presented in this paper applies to ISO/IEC 14443 smart cards of operation mode type A. These smart cards are passive and the inductively coupled RFID transponders have a transceiving range of up to 10 cm.
Contactless and contact smart card systems use the physical constraints of the communication channel to implicitly prove the proximity of a token. These systems, however, are potentially vulnerable to an attack where the attacker relays communication between the .
It executes relay attack using 2 NFC enabled smartphones. One modifies specific bits in transit and another relays it to the terminal by pretending to be a tokenization app (like Google Pay and Apple Pay). A relay attack is a type of interception attack that relays information between two parties without their consent or knowledge. Learn how relay attacks work, how they differ from MITM and replay attacks, and how to prevent them with examples from car theft, SMB, and contactless card scenarios.
A relay attack is a cyber-attack that intercepts and relays communication between two devices to gain unauthorized access. Learn how relay attacks work, see real-life examples, and discover how to protect against them with Twingate.fully executed a relay attack against an ISO 14443A contactless smart card, up to a distance of 50 m. Simply relaying information between the card and reader over a longer distance does not require the same techni-cal resources from the attacker as hardware tampering or cryptanalysis.
An attacker can use a proxy-token and proxy-reader to relay the communication between a legitimate reader and token over a greater distance than intended, thereby tricking the reader into believing that the real token is in close proximity. Learn how relay attacks exploit the communication between legitimate parties and how distance-bounding schemes can prevent them. This chapter covers the concept, mechanisms, and challenges of distance bounding in security of ubiquitous computing systems. Relay attack against a contactless smart card. The concept of relay attack was introduced in the “Grandmaster Chess Attack” scenario [6] . An attacker can win a chess match against a grandmaster without even knowing the rules of the game.
A relay attack is a hacking technique that relays messages between two parties without manipulating them. It can be used to break into a high-security building with a smart card, for example. The relay attack presented in this paper applies to ISO/IEC 14443 smart cards of operation mode type A. These smart cards are passive and the inductively coupled RFID transponders have a transceiving range of up to 10 cm. Contactless and contact smart card systems use the physical constraints of the communication channel to implicitly prove the proximity of a token. These systems, however, are potentially vulnerable to an attack where the attacker relays communication between the .
What is an NFC tag reader? NFC tags can be read with, you guessed, an NFC tag reader. NFC tag readers are NFC-enabled devices that can read the information stored on an NFC tag. The most common NFC readers .Ensure that wireless communication is enabled on your system. Press the POWER button on the NFC Reader. The power LED will turn on blue. If the battery power is getting low the LED will turn red. Place the Nintendo 3DS NFC Reader/Writer and the handheld system on a flat level .
relay attack on smart card|car relay attack examples