smart card authentication step by step These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
Auburn tree poisoner released from jail. OPELIKA, Ala. (AP) — The University of Alabama fan who poisoned Auburn University's landmark oak trees at Toomer's Corner has been released from jail and .Sensa Pens: The Other Type Of Pens Like You Don't See Them Around Anywhere Else http://goo.gl/9UaAIx Auburn radio call - final play of the 2013 Alabama @ Aub.
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Access the free radio live stream and discover more online radio and radio fm stations at a glance. Top Stations. Top Stations. 1 WFAN 66 AM - 101.9 FM. 2 MSNBC. . Classic Rock. Blues. Latin. 90s. R'n'B. Urban. Bossa Nova. .
This step-by-step walkthrough shows you how to set up a basic test environment .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
This step-by-step walkthrough shows you how to set up a basic test environment for using TPM virtual smart cards. After you complete this walkthrough, you'll have a functional virtual smart card installed on the Windows computer. You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this article. Limited support for this configuration is described later in this article.
The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
In this post, we will walk through step-by-step how you can set up and configure new or existing Microsoft PKI to support PIV smart card authentication including setting up an OCSP responder, proper configuration of Active Directory, domain controllers, certificate templates, group policy, and WorkSpaces.Set up smart card logon in Active Directory. This article describes the prerequisites for smart card logon to laptops and servers using Windows. Click the links for instructions how to do the needed configurations.
This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login.
Enabling Smart Card authentication involves the following steps: How does the Authentication Mechanism Work? Workflow. Importing the Root of CA. Mapping User Details. Configuring Status Check for User Certificates. Comparing User Certificates for Verifying Authentication. Enabling Smart Card Authentication. Restarting PAM360 Server & Browser.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart card authentication is highly secure but it has a poor user experience and is costly to deploy and maintain.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. This step-by-step walkthrough shows you how to set up a basic test environment for using TPM virtual smart cards. After you complete this walkthrough, you'll have a functional virtual smart card installed on the Windows computer.
You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this article. Limited support for this configuration is described later in this article.
what is a nfc tag reader used for
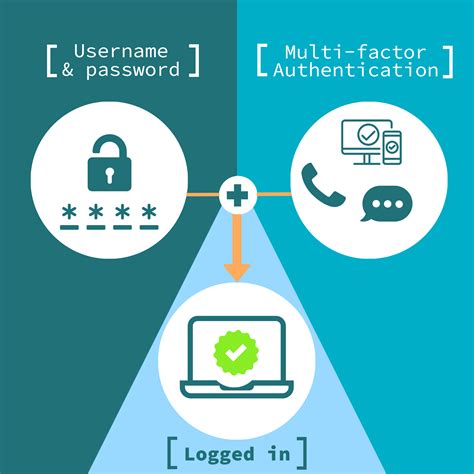
smart card multi factor authentication

The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
In this post, we will walk through step-by-step how you can set up and configure new or existing Microsoft PKI to support PIV smart card authentication including setting up an OCSP responder, proper configuration of Active Directory, domain controllers, certificate templates, group policy, and WorkSpaces.Set up smart card logon in Active Directory. This article describes the prerequisites for smart card logon to laptops and servers using Windows. Click the links for instructions how to do the needed configurations. This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login.
Enabling Smart Card authentication involves the following steps: How does the Authentication Mechanism Work? Workflow. Importing the Root of CA. Mapping User Details. Configuring Status Check for User Certificates. Comparing User Certificates for Verifying Authentication. Enabling Smart Card Authentication. Restarting PAM360 Server & Browser.
smart card identity
whats the nfc tag reader

RAIN RFID inlays, tags and labels work in the Ultra-High Frequency Band and can provide a read range of up to 10 meters or 30 feet. This makes RAIN RFID systems ideal for many tracking applications. Near field communication (NFC) .Limitations. Slightly higher cost: RFID wet inlays are slightly more expensive than dry inlays .
smart card authentication step by step|smart card based identification system