how to best an rfid security tag Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here! Read Bank Card Function : r/flipperzero. r/flipperzero. r/flipperzero. Flipper Zero is a portable multi-tool for pentesters and geeks in a toy-like body. It loves to hack digital stuff around such as radio protocols, access control systems, hardware .digital business card. for free. No designer, printing or app required. Setup within 2 minutes. Add contact info, social accounts, scheduling links, websites and .
0 · two types of rfid tags
1 · rfid tags and their uses
2 · rfid radio frequency identification tags
3 · rfid privacy and security issues
4 · retail anti theft security tags
5 · radio frequency identification tags are
6 · problems with rfid technology
7 · problems with rfid
The answer is simpler than you might expect: the iPhone’s NFC function is enabled or disabled by the apps that require it. So, unlike NFC on Android, where it’s pretty straightforward to turn it on or off directly from the operating system, in iOS, there is no main switch for NFC.
The Ultimate Guide to RF Security Tags: How many types of RF security tags are out there? What are the differences between them, and which ones are right for you and your business? Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here! The Ultimate Guide to RF Security Tags: How many types of RF security tags are out there? What are the differences between them, and which ones are right for you and your business? Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here!
Cover coding. A reader’s signal is louder than a tag’s, making it easier for outsiders to pick up its transmissions. Cover coding takes advantage of this disparity in order to prevent eavesdropping. Initially, the reader requests a random number from the tag and the tag (quietly) responds with this number. RFID security tags are the simplest way for your business to keep track of inventory, shipments, and protect against theft. Small, inexpensive, and effective, if you don’t currently use them then you need to seriously reconsider!
Kill tags possess the ability to permanently disable or render RFID tags inoperable, preventing potential attackers from accessing sensitive information encoded on the tags. Additionally, employing the concept of distance bounding can improve the security of RFID systems by limiting the effective communication range between tags and readers. A Guide to RFID Security Tags. Tracking high-value goods can thwart counterfeiting and supply-chain diversion. Here's what you need to know to choose the best solution for your company. Published: December 1, 2010 Author: Jennifer Zaino. Exploring RFID tag types to find the best solution for your identification and access control needs? Read our breakdown to find your best fit. In this article, we’ll explain how radio frequency identification technology works and how RFID tags are used to track assets as well as fixed inventory. We’ll also walk through some examples of how businesses use RFID asset tags and .
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . The Ultimate Guide to RF Security Tags: How many types of RF security tags are out there? What are the differences between them, and which ones are right for you and your business? Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here!
Cover coding. A reader’s signal is louder than a tag’s, making it easier for outsiders to pick up its transmissions. Cover coding takes advantage of this disparity in order to prevent eavesdropping. Initially, the reader requests a random number from the tag and the tag (quietly) responds with this number.
two types of rfid tags

rfid tags and their uses
RFID security tags are the simplest way for your business to keep track of inventory, shipments, and protect against theft. Small, inexpensive, and effective, if you don’t currently use them then you need to seriously reconsider!Kill tags possess the ability to permanently disable or render RFID tags inoperable, preventing potential attackers from accessing sensitive information encoded on the tags. Additionally, employing the concept of distance bounding can improve the security of RFID systems by limiting the effective communication range between tags and readers.

A Guide to RFID Security Tags. Tracking high-value goods can thwart counterfeiting and supply-chain diversion. Here's what you need to know to choose the best solution for your company. Published: December 1, 2010 Author: Jennifer Zaino.
Exploring RFID tag types to find the best solution for your identification and access control needs? Read our breakdown to find your best fit. In this article, we’ll explain how radio frequency identification technology works and how RFID tags are used to track assets as well as fixed inventory. We’ll also walk through some examples of how businesses use RFID asset tags and . This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
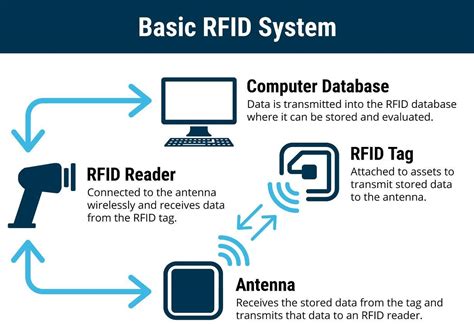
rfid radio frequency identification tags

chips in rfid tags usually can function as a processor
This can also be purchased on the above shopping platform. Open the Mtools application. Plug in the ACR122u in your android smartphone with the OTG adapter. Click the “+” Icon. Place the card onto the reader. The card is .Custom Animal Crossing Amiibo Cards. ALL Series are Available in our store. Fast Ship from .
how to best an rfid security tag|retail anti theft security tags