oid smart card logon Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 . Go to NFC -> Detect Reader -> hold flipper to your front door lock. plug your flipper into your computer or use the mobile app/bluetooth . Go to NFC Tools -> mfkey32 to read and calculate keys scan the fob again. should read the tag .Most of the time these NFC cards are using encryption so it is not possible to emulate them unless you can figure out the encryption key used. And finding the encryption key would make the whole system insecure, because the purpose of these cards is to provide controlled access, .
0 · certificates
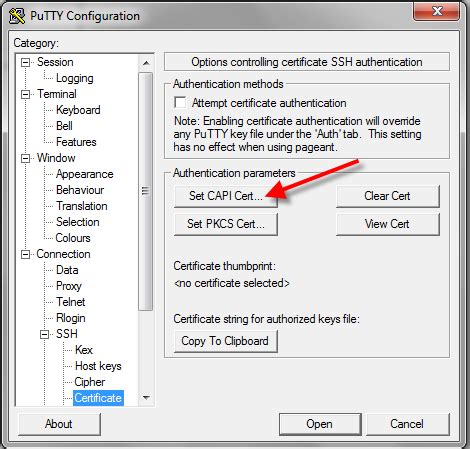
1 · Smart Card Logon for SSH
2 · Problems with authentication on domain using smart card logon
3 · Object Identifiers (OID) in PKI
4 · Generating a self
5 · Enabling smart card logon
6 · Configure Smart Card Logon on Windows Domains
7 · Certificate Requirements and Enumeration
8 · Certificate
The NFL playoff picture is already shifting in Week 11, with the Eagles rising to the NFC East lead and No. 2 seed as the Commanders fall. . wild card No. 1: Their defensive .
Client Authentication (1.3.6.1.5.5.7.3.2) (The client authentication OID) is only required if a certificate is used for SSL authentication.) Smart Card Logon (1.3.6.1.4.1.311.20.2.2) Subject .

To allow smart card logon within an Active Directory domain the smart card’s chain of trust m.To allow smart card logon within an Active Directory domain the smart card’s chain of trust must support the Smart Card Logon (OID 1.3.6.1.4.1.311.20.2.2) and Client Authentication (OID .These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical . Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 .
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for . After latest Servicing Stack update (KB4586863) and Cumulative update (KB4586786), logon with smart card stopped working with this message: "This smart card .
If you get a prompt to enter your password, select Use a certificate or smart card and select Sign in. Select the correct cert in the certificate picker UI and select OK . You should now be signed .The most common OID in most PKI environments is Microsoft’s OID: 1.3.6.1.4.1.311. That is the ARC for Microsoft, which is the base value. In a Windows-based PKI when the first ADCS role .
For sign-in to work in a smart card-based domain, the smart card certificate must meet the following conditions: The KDC root certificate on the smart card must have an HTTP .
Client Authentication (1.3.6.1.5.5.7.3.2) (The client authentication OID) is only required if a certificate is used for SSL authentication.) Smart Card Logon (1.3.6.1.4.1.311.20.2.2) Subject Alternative Name = Other Name: Principal Name= (UPN). For example: UPN = [email protected]. You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this article. Limited support for this configuration is described later in this article.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
To allow smart card logon within an Active Directory domain the smart card’s chain of trust must support the Smart Card Logon (OID 1.3.6.1.4.1.311.20.2.2) and Client Authentication (OID 1.3.6.1.5.5.7.3.2) application policies. Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 security key such as the Yubikey 5 NFC.Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.If you get a prompt to enter your password, select Use a certificate or smart card and select Sign in. Select the correct cert in the certificate picker UI and select OK . You should now be signed into the Azure portal.
The most common OID in most PKI environments is Microsoft’s OID: 1.3.6.1.4.1.311. That is the ARC for Microsoft, which is the base value. In a Windows-based PKI when the first ADCS role is added, a unique OID is generated to convey each individual instance of a PKI. For sign-in to work in a smart card-based domain, the smart card certificate must meet the following conditions: The KDC root certificate on the smart card must have an HTTP CRL distribution point listed in its certificate; The smart card sign-in certificate must have the HTTP CRL distribution point listed in its certificate To allow smart card logon within an Active Directory domain the smart card’s chain of trust must support the Smart Card Logon (OID 1.3.6.1.4.1.311.20.2.2) and Client Authentication (OID 1.3.6.1.5.5.7.3.2) application policies.Client Authentication (1.3.6.1.5.5.7.3.2) (The client authentication OID) is only required if a certificate is used for SSL authentication.) Smart Card Logon (1.3.6.1.4.1.311.20.2.2) Subject Alternative Name = Other Name: Principal Name= (UPN). For example: UPN = [email protected].
You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this article. Limited support for this configuration is described later in this article.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
To allow smart card logon within an Active Directory domain the smart card’s chain of trust must support the Smart Card Logon (OID 1.3.6.1.4.1.311.20.2.2) and Client Authentication (OID 1.3.6.1.5.5.7.3.2) application policies. Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 security key such as the Yubikey 5 NFC.Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.If you get a prompt to enter your password, select Use a certificate or smart card and select Sign in. Select the correct cert in the certificate picker UI and select OK . You should now be signed into the Azure portal.
The most common OID in most PKI environments is Microsoft’s OID: 1.3.6.1.4.1.311. That is the ARC for Microsoft, which is the base value. In a Windows-based PKI when the first ADCS role is added, a unique OID is generated to convey each individual instance of a PKI.
certificates
For sign-in to work in a smart card-based domain, the smart card certificate must meet the following conditions: The KDC root certificate on the smart card must have an HTTP CRL distribution point listed in its certificate; The smart card sign-in certificate must have the HTTP CRL distribution point listed in its certificate

smart card handbook pdf
 in PKI .jpg)
• Flashibo, NFC Tag, Auto-Regen UID (Black) 4.4 out of 5 stars. 112. 500+ .
oid smart card logon|Generating a self