rfid security system project pdf © 2008-2024 ResearchGate GmbH. All rights reserved. Terms; Privacy; IP . My iPhone XS Max (iOS 14 b4) can only read tags when I turn it off and on. After it reads 1, it can't read another, so for instance, I can create a shortcut automation but I can not use the tag .
0 · rfid systems
1 · rfid security vulnerabilities
2 · rfid security system
3 · rfid security problems
4 · rfid security and access control
5 · rfid handbook PDF
6 · rfid based security system PDF
7 · rfid access control system PDF
To read the UID of an NFC tag with a Windows computer, you need an NFC reader/writer and the software NFC21 Tools. Connect the NFC reader/writer to your computer via USB and then start the NFC21 Reader .
With the help of histogram of oriented gradients (HOG), face recognition algorithm, RFID, and one-time passcode on registered email id, an intruder-free security system can be .© 2008-2024 ResearchGate GmbH. All rights reserved. Terms; Privacy; IP .The purpose of an RFID system is transmitting data from a portable device, called a tag, to an RFID reader to execute a particular application based on the tag provided identification or . With the help of histogram of oriented gradients (HOG), face recognition algorithm, RFID, and one-time passcode on registered email id, an intruder-free security system can be achieved.
The purpose of an RFID system is transmitting data from a portable device, called a tag, to an RFID reader to execute a particular application based on the tag provided identification or location information (Graafstra, 2006; O' Brien, 2006).
current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this paper, we discuss four common types of RFID tag attacks .
[RFID Handbuch. English] Fundamentals and Applications in Contactless Smart Cards, Radio Frequency Identification and Near-Field Communication, Third Edition / Klaus Finkenzeller ; translated by Dorte M¨ ¨uller. – 3rd ed. p. cm. Includes index. ISBN 978-0-470-69506-7 (cloth) 1. Inventory control–Automation. 2. Radio frequency .
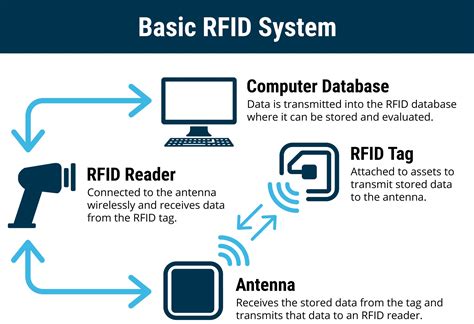
CHAPTER-1: INTRODUCTION. 1.1 Introduction to RFID security system. 1.2 Aim of the project. 1.3 Technical Approach. 1.4 Hardware Description. This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy.
RFID SMART DOOR LOCK SECURITY SYSTEM. A Project and Thesis submitted in partial fulfilment of the requirements for the Award of Degree of Bachelor of Science in Electrical and Electronic Engineering. Submitted by. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
RFID Based Security System. K.Srinivasa Ravi, G.H.Varun, T.Vamsi, P.Pratyusha. Abstract— Radio Frequency Identification (RFID) is one member in the family of Automatic Identification and Data Capture (AIDC) technologies and is a fast and .
RFID based security and access control system is more secure and fast responded as compared to the other system like biometric. The advantage of the RFID system is contact-less and works without-line-of-sight. By using arduino it is easy to access and works very quickly while burning the code it is like plug and play device. Users can With the help of histogram of oriented gradients (HOG), face recognition algorithm, RFID, and one-time passcode on registered email id, an intruder-free security system can be achieved.The purpose of an RFID system is transmitting data from a portable device, called a tag, to an RFID reader to execute a particular application based on the tag provided identification or location information (Graafstra, 2006; O' Brien, 2006).
current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this paper, we discuss four common types of RFID tag attacks .[RFID Handbuch. English] Fundamentals and Applications in Contactless Smart Cards, Radio Frequency Identification and Near-Field Communication, Third Edition / Klaus Finkenzeller ; translated by Dorte M¨ ¨uller. – 3rd ed. p. cm. Includes index. ISBN 978-0-470-69506-7 (cloth) 1. Inventory control–Automation. 2. Radio frequency .CHAPTER-1: INTRODUCTION. 1.1 Introduction to RFID security system. 1.2 Aim of the project. 1.3 Technical Approach. 1.4 Hardware Description.
This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy.RFID SMART DOOR LOCK SECURITY SYSTEM. A Project and Thesis submitted in partial fulfilment of the requirements for the Award of Degree of Bachelor of Science in Electrical and Electronic Engineering. Submitted by. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.RFID Based Security System. K.Srinivasa Ravi, G.H.Varun, T.Vamsi, P.Pratyusha. Abstract— Radio Frequency Identification (RFID) is one member in the family of Automatic Identification and Data Capture (AIDC) technologies and is a fast and .
very high temperature rfid tags
A few months ago I was requested to make an app to read/write from/to Non-NDEF NFC Tags. While, according to the official Android reference, for the standard NDEF Tags you .13. First of all you have to get permission in AndroidManifest.xml file for NFC. The permissions are: .
rfid security system project pdf|rfid security and access control