radio frequency identification rfid protection An industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need. NFC interactor is a powerful Near Field Communication tag reader / writer app, aimed at enthusiasts and developers. NFC Tag Reading and NDEF Parsing Tap NFC tags to analyze their real contents.RFID NFC Reader Writer 13.56MHZ USB Contactless/Contact Smart Card Reader+2 Pcs 4442 Cards +2 Pcs Ntag213 Labels+ Free sdk : Amazon.in: Electronics . USB Charged RFID Reader Writer, ID Card Copier Duplicate, NFC Access Control Card, Full Encryption Decode, .
0 · what is an rfid system
1 · rfid radio frequency identification systems
2 · rfid radio frequency identification readers
3 · rfid is involved when using
4 · radio frequency tracking
5 · radio frequency identification rfid definition
6 · radio frequency identification rfid 1970s
7 · explain rfid in detail
Instant Reviews with a Simple NFC Swipe. Watch the video and see how a quick swipe of our NFC card allows customers to instantly share their 5-star experiences. Unlock greater engagement, improve visibility on Google and .Top 8 Benefits of Custom NFC Business Cards for Professionals. In today’s digital-first business world, custom NFC business cards are reshaping how professionals share their contact details, network, and make lasting impressions. These tech-savvy cards offer far more .
An industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need. RFID blocking is the process of making your RFID-enabled device resistant to unauthorized access. The most popular way to achieve this is by getting an RFID blocking . An industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need.
RFID blocking is the process of making your RFID-enabled device resistant to unauthorized access. The most popular way to achieve this is by getting an RFID blocking wallet — a holder for your cards that is made from materials that interfere with electromagnetic fields.
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. RFID-blocking wallets are supposed to prevent your RFID card information from being stolen. But do they really work? Even then, is the danger real enough to make a purchase worth it?RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
Learn all about RFID blocking technology and why you should care. Find out how this simple security measure can help keep your personal info safe. Quick Links. How RFID Works. Common Uses of RFID. Security and Privacy Concerns. RFID is a technology that surrounds us every day. It's in our credit cards, passports, and some of the products we buy. Even many of our pets have RFID chips in them! RFID is essentially a form of electronic bar tag -- one that can be much smaller. RFID—or radio frequency identification—theft is a rare occurrence, but it does happen in high-traffic areas. RFID-blocking technology is essentially a fabric material that blocks scanners. This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.
what is an rfid system
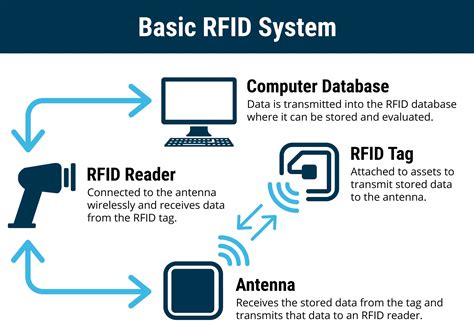
An industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need. RFID blocking is the process of making your RFID-enabled device resistant to unauthorized access. The most popular way to achieve this is by getting an RFID blocking wallet — a holder for your cards that is made from materials that interfere with electromagnetic fields.
smart online loading using dibet card bdo
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. RFID-blocking wallets are supposed to prevent your RFID card information from being stolen. But do they really work? Even then, is the danger real enough to make a purchase worth it?RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
Learn all about RFID blocking technology and why you should care. Find out how this simple security measure can help keep your personal info safe. Quick Links. How RFID Works. Common Uses of RFID. Security and Privacy Concerns. RFID is a technology that surrounds us every day. It's in our credit cards, passports, and some of the products we buy. Even many of our pets have RFID chips in them! RFID is essentially a form of electronic bar tag -- one that can be much smaller. RFID—or radio frequency identification—theft is a rare occurrence, but it does happen in high-traffic areas. RFID-blocking technology is essentially a fabric material that blocks scanners.
rfid radio frequency identification systems
This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.
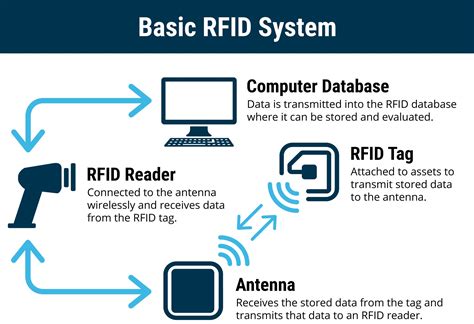
rfid radio frequency identification readers


smart national id card bangladesh check
smart media card 4mb 5v
Scores, game details, and how to watch.
radio frequency identification rfid protection|radio frequency identification rfid definition