smart card trusted root Root certificate propagation provides the ability to use the smart card to include the missing trust chain. When the smart card is inserted, the certificate propagation service . $26.99
0 · view certs on smart card
1 · smart card trusted roots store
2 · smart card log on certificate
3 · smart card certificate authentication
4 · read certificate from smart card
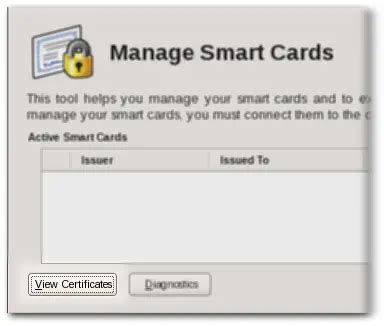
5 · manage smart card certificates
6 · join domain with smart card
7 · import certificates from smart card
The NFC chip UID is read by a device from an NFC chip either by reading a specific portion of memory, by calling an NFC chip command or from a software subsystem that performs one of .
You can enable a smart card logon process with Microsoft Windows 2000 and a non-Microsoft certification authority (CA) by following the guidelines in this . See more
Root certificate propagation provides the ability to use the smart card to include the missing trust chain. When the smart card is inserted, the certificate propagation service .
view certs on smart card
smart card trusted roots store
After latest Servicing Stack update (KB4586863) and Cumulative update (KB4586786), logon with smart card stopped working with this message: "This smart card . However, when I try to login back again using a smart card, it says "The Smart card certificate used for authentication was not trusted". I checked my event logs, specifically . I used different little tools to see informations (ATR etc.) about my smartcard and they all worked out. I can see a lot of certificates there, but the one from my smartcard is . In order for this to work, all the CA’s in the path must be trusted by “Domain B”. For instance, let’s say you have a Root CA and a couple of intermediate CA’s: Root CA > CA1 > .
1. When trying to import a certificate into the User trusted root certificate store we get the error: “The import failed because the store was read-only, the store was full, or the .Now that we've switched to smart-card authentication, our usernames and passwords aren't functional anymore as expected (smart-card required for interactive login in AD), however, . 1 Answer. Sorted by: 14. I managed to solve a similar problem I was having by following the instructions here (here adapting steps 3 and 12 to read "Trusted Root . Smart card root certificate requirements for use with domain sign-in. For sign-in to work in a smart card-based domain, the smart card certificate must meet the following .
Export or download the third-party root certificate. How to obtaining the party root certificate varies by vendor. The certificate must be in Base64 Encoded X.509 format. Add the third-party root CA to the trusted roots in an Active Directory Group Policy object. Root certificate propagation provides the ability to use the smart card to include the missing trust chain. When the smart card is inserted, the certificate propagation service propagates any root certificates on the card to the trusted smart card . After latest Servicing Stack update (KB4586863) and Cumulative update (KB4586786), logon with smart card stopped working with this message: "This smart card could not be used. Additional detail may be available in the .
However, when I try to login back again using a smart card, it says "The Smart card certificate used for authentication was not trusted". I checked my event logs, specifically security and CAPI2 but nothing correspond with the specific smart card login. I used different little tools to see informations (ATR etc.) about my smartcard and they all worked out. I can see a lot of certificates there, but the one from my smartcard is missing in the store. The folder 'Smartcard trusted Roots' is empty. In order for this to work, all the CA’s in the path must be trusted by “Domain B”. For instance, let’s say you have a Root CA and a couple of intermediate CA’s: Root CA > CA1 > CA2 > device cert. The Root CA, CA1 and CA2 would need to be trusted by anyone that’s going to be validating that certificate.
1. When trying to import a certificate into the User trusted root certificate store we get the error: “The import failed because the store was read-only, the store was full, or the store did not open correctly" CertMgr error. Now that we've switched to smart-card authentication, our usernames and passwords aren't functional anymore as expected (smart-card required for interactive login in AD), however, we're unable to add our computers to the domain now with our smart-cards. 1 Answer. Sorted by: 14. I managed to solve a similar problem I was having by following the instructions here (here adapting steps 3 and 12 to read "Trusted Root Certification Authorities" instead of "Trusted Publishers"): Download and save the certificate. Open the Certificate Manager.Smart Card Trusted Roots (SmartCardRoot) — This container is used to store trusted smart card certificates. Other People (AddressBook) — This container maintains certificates that have been added to an Outlook contact.
smart card log on certificate
Export or download the third-party root certificate. How to obtaining the party root certificate varies by vendor. The certificate must be in Base64 Encoded X.509 format. Add the third-party root CA to the trusted roots in an Active Directory Group Policy object. Root certificate propagation provides the ability to use the smart card to include the missing trust chain. When the smart card is inserted, the certificate propagation service propagates any root certificates on the card to the trusted smart card . After latest Servicing Stack update (KB4586863) and Cumulative update (KB4586786), logon with smart card stopped working with this message: "This smart card could not be used. Additional detail may be available in the . However, when I try to login back again using a smart card, it says "The Smart card certificate used for authentication was not trusted". I checked my event logs, specifically security and CAPI2 but nothing correspond with the specific smart card login.
I used different little tools to see informations (ATR etc.) about my smartcard and they all worked out. I can see a lot of certificates there, but the one from my smartcard is missing in the store. The folder 'Smartcard trusted Roots' is empty. In order for this to work, all the CA’s in the path must be trusted by “Domain B”. For instance, let’s say you have a Root CA and a couple of intermediate CA’s: Root CA > CA1 > CA2 > device cert. The Root CA, CA1 and CA2 would need to be trusted by anyone that’s going to be validating that certificate.
1. When trying to import a certificate into the User trusted root certificate store we get the error: “The import failed because the store was read-only, the store was full, or the store did not open correctly" CertMgr error.
Now that we've switched to smart-card authentication, our usernames and passwords aren't functional anymore as expected (smart-card required for interactive login in AD), however, we're unable to add our computers to the domain now with our smart-cards. 1 Answer. Sorted by: 14. I managed to solve a similar problem I was having by following the instructions here (here adapting steps 3 and 12 to read "Trusted Root Certification Authorities" instead of "Trusted Publishers"): Download and save the certificate. Open the Certificate Manager.

smart card certificate authentication

read certificate from smart card
manage smart card certificates
join domain with smart card
ufr-examples-android-nfc_data_exchange_through_card_emulation ufr-examples-android-nfc_data_exchange_through_card_emulation Public Android source code example of using uFR nfc data exchange through card emulation. uFR reader .
smart card trusted root|manage smart card certificates