authenticate with smart cards Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you . Writing a URL to a blank NFC chip is arguably a lot easier than setting up your digital profile, as you will soon find out. Open the NFC Tools app and select Write from the main menu, . See more
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Ensure that you have given the necessary permissions for the app to access your iPhone’s NFC functionality. Place the RFID Card Near the iPhone: With the NFC writer app open, place your RFID card near the back of your .My College decided to switch to using NFC card entry to the buildings instead if the old swipe entry. Unfortunately, the new cards appear to contain the world's worst NFC chip that only works the 50th try. I was wondering if there was a way for me to transfer the information to my phone .
Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter. Understanding Smart Card Authentication: Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information. It contains data that identifies the cardholder.
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers. With contact cards, the embedded chip is inserted into the reader and makes physical contact for the transmission of data.
And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second coming, a revival brought on by recent mobile and cloud support in Microsoft Azure.
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter. Understanding Smart Card Authentication: Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information. It contains data that identifies the cardholder.
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers. With contact cards, the embedded chip is inserted into the reader and makes physical contact for the transmission of data. And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second coming, a revival brought on by recent mobile and cloud support in Microsoft Azure.
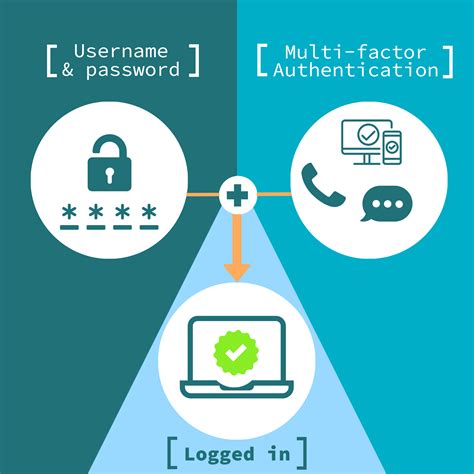
smart card multi factor authentication
smart card identity

smart card based identification system
smart card authentication step by
smart card authentication protocol

cœurs corazones cœur corazón cuore cuori hart harten. Brand New. C $10.31. Buy It Now +C .
authenticate with smart cards|smart card authentication protocol