implement two-factor authentication with smart cards HOW IT WORKS. There are three categories of credentials: something you either know, have, or are. Here are some examples in each. category. In order to gain access, your credentials must come from at least two different categories. One of the most common methods is to login using your user name and password.
Amiibo cards are ridiculously simple, and only need a few things: –Tagmo for an Android with NFC functionality, or other methods without .
0 · vsc for smart card db
1 · virtual smart card windows 11
2 · virtual smart card windows 10
3 · virtual smart card rdp
4 · tpm virtual smart card management
5 · smart card invalid signature
6 · smart card for bitlocker
7 · smart card 2 factor authentication
Using Wallet.app to open doors with NFC reader. G'day. At my office the doors are locked with .
Smart Cards¶ Smartcards are credit-card size cards with a chip containing a digital certificate for the user, which is unlocked with a PIN. They are commonly used for operating system .
Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience .
vsc for smart card db
virtual smart card windows 11
Physical smart cards and virtual smart cards offer comparable levels of security. They both implement two-factor authentication for using network resources. However, they differ in certain aspects, including physical security and the practicality of an attack. Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy.Smart Cards¶ Smartcards are credit-card size cards with a chip containing a digital certificate for the user, which is unlocked with a PIN. They are commonly used for operating system authentication, but are rarely used in web applications.HOW IT WORKS. There are three categories of credentials: something you either know, have, or are. Here are some examples in each. category. In order to gain access, your credentials must come from at least two different categories. One of the most common methods is to login using your user name and password.
After virtual smart cards are created, personalized, and provisioned, they can be used for convenient two-factor authentication. Deployment administrators must be aware of several common administrative scenarios, which can be approached by using a purchased virtual smart card solution or on a case-by-case basis with in-house methods.An account secured with 2FA typically requires an individual to authenticate using something they know— typically a password—as well as something they have, such as a cell phone or hardware token. Many 2FA methods in widespread use today have not been subjected to .Two-factor authentication adds an extra layer of security to the authentication process by making it harder for attackers to gain access to a person's devices or online accounts. Even if the victim's password is hacked, a password alone isn't enough to pass the authentication check. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
Step 1. Go to My Sign-Ins | Security Info | Microsoft.comnt. Step 2. Sign into your account. Make sure at the left hand of your screen, you are on Security info. Note: This page will look different for you, before I hid my email address and device name the previous Authenticator App is connected to. Step 3. Click on Add sign-in method. Step 4.2FA implementation. Implementing 2FA within a business or personal setting is beneficial in protecting vulnerable networks and databases. With a mobile device, you can generate your own codes, or tokens, to provide a unique set of letters/numbers to verify your identity. Physical smart cards and virtual smart cards offer comparable levels of security. They both implement two-factor authentication for using network resources. However, they differ in certain aspects, including physical security and the practicality of an attack.
Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy.Smart Cards¶ Smartcards are credit-card size cards with a chip containing a digital certificate for the user, which is unlocked with a PIN. They are commonly used for operating system authentication, but are rarely used in web applications.HOW IT WORKS. There are three categories of credentials: something you either know, have, or are. Here are some examples in each. category. In order to gain access, your credentials must come from at least two different categories. One of the most common methods is to login using your user name and password.
After virtual smart cards are created, personalized, and provisioned, they can be used for convenient two-factor authentication. Deployment administrators must be aware of several common administrative scenarios, which can be approached by using a purchased virtual smart card solution or on a case-by-case basis with in-house methods.An account secured with 2FA typically requires an individual to authenticate using something they know— typically a password—as well as something they have, such as a cell phone or hardware token. Many 2FA methods in widespread use today have not been subjected to .Two-factor authentication adds an extra layer of security to the authentication process by making it harder for attackers to gain access to a person's devices or online accounts. Even if the victim's password is hacked, a password alone isn't enough to pass the authentication check. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
virtual smart card windows 10
Step 1. Go to My Sign-Ins | Security Info | Microsoft.comnt. Step 2. Sign into your account. Make sure at the left hand of your screen, you are on Security info. Note: This page will look different for you, before I hid my email address and device name the previous Authenticator App is connected to. Step 3. Click on Add sign-in method. Step 4.
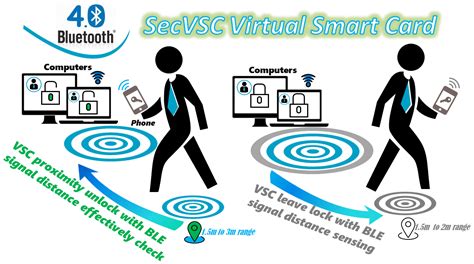
virtual smart card rdp
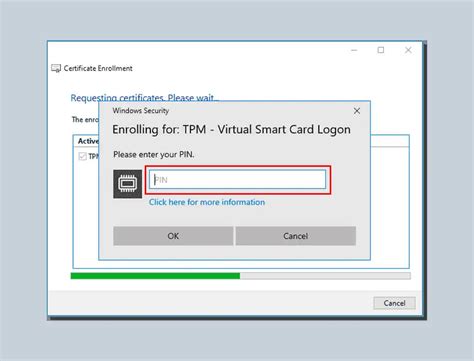
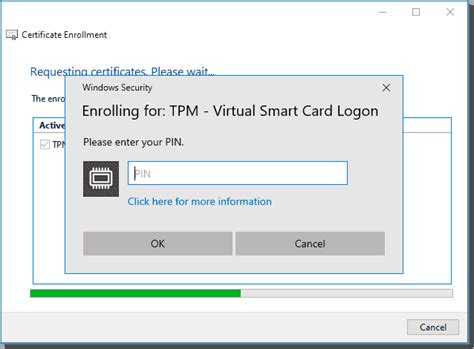
tpm virtual smart card management
smart card invalid signature
smart card for bitlocker
Sunday, January 14, 2024. NFC Wild Card Game; Sun 1/14 1 2 3 4 FINAL; Green Bay (9-8): 7: 20: Pass
implement two-factor authentication with smart cards|smart card 2 factor authentication