rfid security system ppt The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random . of. Touchless. Networking. All ZCard Cards come pre-loaded with a free digital profile, contact .
0 · rfid technology ppt presentation
1 · rfid technology ppt
2 · rfid tags for library books
3 · rfid system in library
4 · rfid ppt download
5 · rfid in library management system
6 · radio frequency identification ppt
7 · library automation using rfid
See the final scores and stats of the four 2013 NFL wild card games, including the Saints vs Eagles, Chargers vs Bengals, and 49ers vs Packers. Find out who advanced to the divisional round and who went home.
The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for . This document presents a project on an RFID-based security access control system. It includes sections that describe what RFID cards are, the invention of RFID technology, different types of RFID cards, a block diagram .
what are rfid tags used for select the best answer
The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random . The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for organizations by only allowing access to people with valid RFID tags. This document presents a project on an RFID-based security access control system. It includes sections that describe what RFID cards are, the invention of RFID technology, different types of RFID cards, a block diagram of the system components, how the power supply works, descriptions of components like the LCD display and buzzer, how access is .
The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random number generation on tags to address security challenges in RFID systems. Read more.
what generation rfid is the discoverit card
Guidelines for securing radio frequency identification (RFID) systems Recommendations of the National Institute of Standards and Technology, NIST 800-98, 2007. Security coordinates Enhanced Security: Integrating RFID and NFC with existing security systems strengthens overall security. RFID tags and NFC-enabled devices can be programmed with unique identifiers, reducing the risk of unauthorized access.This document describes an RFID-based door security system using an 8051 microcontroller and EM-18 RFID module. The system provides security to organizations by only allowing authorized personnel with valid RFID tags.From Smart Homes to Smart Cities: Integrating RFID for Enhanced Security - Let's look at how RFID is helping to improve security everywhere from our homes to the bustling streets of smart cities. | PowerPoint PPT presentation | free to view
what does the rfid chip do in my credit card
This topic generally describes about the security and privacy mechanism in RFID multi domain which is further divided into three sub topics that is RFID forehand system security, RFID backhand system security and RFID inter domain system security.
This topic generally describes about the security and privacy mechanism in RFID multi domain which is further divided into three sub topics that is RFID forehand system security, RFID backhand system security and RFID inter domain system security.RFID SECURITY SYSTEM - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. RFID is a wireless automatic identification method using Radio Waves. The system uses an RFID reader and tags to identify authorized users and grant access by controlling a relay if their RFID code matches stored codes. An LCD displays status messages. The system provides security for organizations by only allowing access to people with valid RFID tags. This document presents a project on an RFID-based security access control system. It includes sections that describe what RFID cards are, the invention of RFID technology, different types of RFID cards, a block diagram of the system components, how the power supply works, descriptions of components like the LCD display and buzzer, how access is .
The document outlines security risks like spoofing, replay attacks, and unauthorized tracking. It emphasizes the need for lightweight cryptography and random number generation on tags to address security challenges in RFID systems. Read more.
Guidelines for securing radio frequency identification (RFID) systems Recommendations of the National Institute of Standards and Technology, NIST 800-98, 2007. Security coordinates
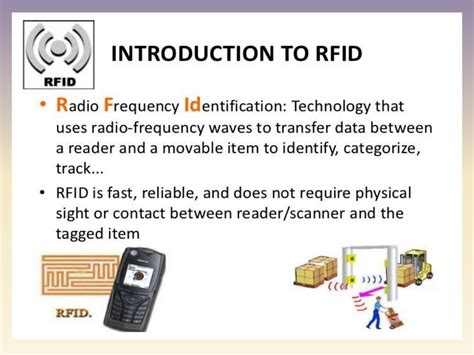
Enhanced Security: Integrating RFID and NFC with existing security systems strengthens overall security. RFID tags and NFC-enabled devices can be programmed with unique identifiers, reducing the risk of unauthorized access.This document describes an RFID-based door security system using an 8051 microcontroller and EM-18 RFID module. The system provides security to organizations by only allowing authorized personnel with valid RFID tags.
rfid technology ppt presentation
rfid technology ppt
From Smart Homes to Smart Cities: Integrating RFID for Enhanced Security - Let's look at how RFID is helping to improve security everywhere from our homes to the bustling streets of smart cities. | PowerPoint PPT presentation | free to view This topic generally describes about the security and privacy mechanism in RFID multi domain which is further divided into three sub topics that is RFID forehand system security, RFID backhand system security and RFID inter domain system security.
This topic generally describes about the security and privacy mechanism in RFID multi domain which is further divided into three sub topics that is RFID forehand system security, RFID backhand system security and RFID inter domain system security.
rfid tags for library books

what is rfid card protector
what are rfid credit card sleeves
To use them: plug your FlipperZero into your computer- open your preferred file manager- navigate to /NFC/- drag-and-drop the Amiibo folder to there. Now when you select the NFC function on the Flipper you can select which .nfc file you .You will receive the sturdy plastic NFC card that will bring your favorite villager to your .
rfid security system ppt|rfid technology ppt presentation