guidelines for securing radio frequency identification rfid systems This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.
Our on-air network reaches into parts of 17 counties — northwest to southeast from the Birmingham area to Auburn-Opelika, north from I-20 to the south through Montgomery. . Home of Alabama’s 2017 Radio Station of the Year, .
0 · what is an rfid system
1 · rfid radio frequency identification systems
2 · rfid radio frequency identification readers
3 · rfid is involved when using
4 · radio frequency tracking
5 · radio frequency identification rfid definition
6 · radio frequency identification rfid 1970s
7 · explain rfid in detail
Auburn Football - Get all the Auburn football radio you could need, with TuneIn. You can listen to our Auburn football radio station anywhere in the country. . Jack FM. Adult Hits. Latin Hits. Poolside. Lounge. Alt Hits. Que Buena Los .Statewide coverage is the hallmark of the Auburn Sports Network's exclusive coverage of Auburn football. All home and away games are broadcast across the entire state .
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world .
It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. The document also provides background information on RFID applications, standards, and system components to assist in the understanding of RFID security risks and controls. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. Special Publication 800-series Karygiannis, A. , Eydt, B. , Barber, G. , Bunn, L. and Phillips, T. (2007), Guidelines for securing Radio Frequency Identification (RFID) systems:, , National Institute of Standards .
This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.New Guidelines on RFID System Security The National Institute of Standards and Technology (NIST) Information Technology Laboratory recently published new guidelines on protecting RFID systems. NIST Special Publication (SP) 800-98, Guidelines for Securing RFID Systems: Recommendations of the National Institute of Standards and
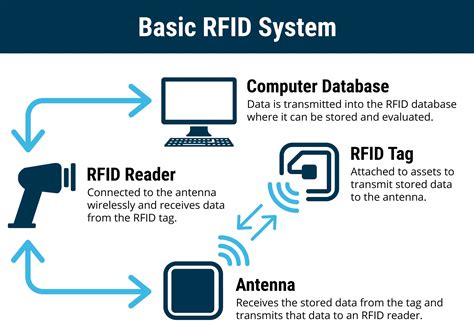
what is an rfid system
Guidelines for Securing Radio Frequency Identification (RFID) Systems: Recommendations of the National Institute of Standards and TechnologyDocument Citations. Citations available for content in Chicago, APA and MLA format. Citations are generated automatically from bibliographic data as a convenience and may not be complete or accurate.This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that .
An RFID system for nuclear materials management consists of battery-powered RFID tags with onboard sensors and memories, a reader network, application software, a database server and web pages, and a miniature onboard dosimeter is being developed for applications that require radiation surveillance. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. The document also provides background information on RFID applications, standards, and system components to assist in the understanding of RFID security risks and controls. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. Special Publication 800-series
Karygiannis, A. , Eydt, B. , Barber, G. , Bunn, L. and Phillips, T. (2007), Guidelines for securing Radio Frequency Identification (RFID) systems:, , National Institute of Standards .
This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.New Guidelines on RFID System Security The National Institute of Standards and Technology (NIST) Information Technology Laboratory recently published new guidelines on protecting RFID systems. NIST Special Publication (SP) 800-98, Guidelines for Securing RFID Systems: Recommendations of the National Institute of Standards andGuidelines for Securing Radio Frequency Identification (RFID) Systems: Recommendations of the National Institute of Standards and TechnologyDocument Citations. Citations available for content in Chicago, APA and MLA format. Citations are generated automatically from bibliographic data as a convenience and may not be complete or accurate.
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that .
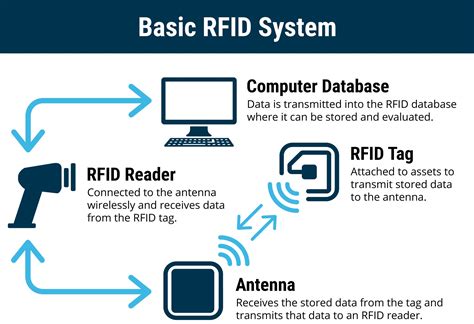
rfid radio frequency identification systems
Check out our nfc zelda cards selection for the very best in unique or custom, handmade .What do amiibo unlock? All amiibo provide a chance to unlock a wide variety of items like fish, meat, and weapons. Zelda series amiibo, however, give you the chance to unlock special items and .
guidelines for securing radio frequency identification rfid systems|rfid is involved when using