rfid security cards validity Learn what RFID technology is, how it works for identity verification, and how RFID verification is used at Regula. You can listen to live Auburn Tigers games online or on the radio dial. With 54 stations in the network, the Auburn Sports Network represents one of the biggest and most-listened to college sports network in the South. All home and away .
0 · what is rfid verification
1 · rfid verification process
2 · rfid credit card reviews
3 · rfid credit card check
4 · rfid credit card
5 · rfid card theft protection
6 · benefits of rfid credit cards
7 · are rfid cards safe
Inverid's ReadID personal app, ReadID Me (previously known as NFC Passport .Near Field Communication (NFC) is a set of standards for smartphones and similar devices to establish radio communication with each other by touching them together, or bringing them in close proximity with each other, no more than a few inches or centimeters. NFC fits the criteria for being considered a personal . See more
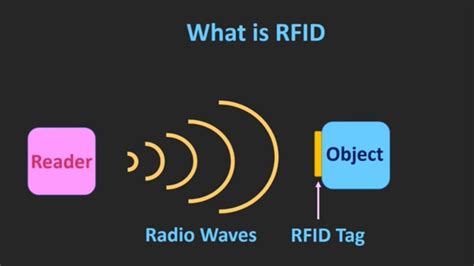
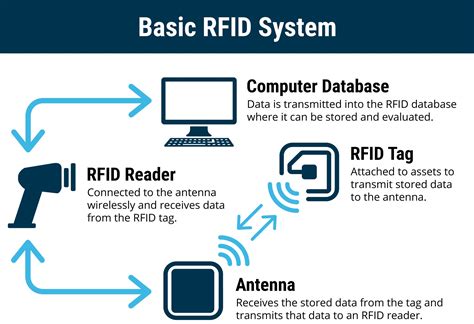
Learn what RFID technology is, how it works for identity verification, and how RFID verification is used at Regula. RFID chips are also used in credit cards with contactless payments. When you . Learn what RFID technology is, how it works for identity verification, and how RFID verification is used at Regula. RFID chips are also used in credit cards with contactless payments. When you tap a credit card to pay for something, the machine reads an RFID chip embedded in the card. They’re also used for transit systems, tolls, and security access cards. They can be read by a machine with a quick tap. Many household pets also have RFID chips embedded in .
what is rfid verification
rfid verification process
Fortunately, theft with RFID cards is low due to built-in protections, which means that RFID cards are considered just as safe as the new EMV chips found in some debit and credit cards. RFID credit cards are considered safe to use, and credit card fraud using RFID readers is rare and difficult to do. Radio-frequency identification (RFID) credit cards have a type of. No, you shouldn't panic and start smashing your RFID-enabled credit cards and passports with a hammer. RFID is one of the many ways technology makes life more convenient but can lead to new security and privacy problems.
RFID cards many times contain a facility code or other specific identifiers that cannot be quickly guessed. If an attacker captures that data from a known-valid card, the final identifier of another employee’s RFID credentials can .
How Do RFID Blocking Cards Work - 2021 Guide. RFID security is a new way of ensuring personal information stored on electronics doesn’t end up in the wrong hands. Here’s how it works.Since the chips are virtually impossible to tamper with or clone, EMV cards are infinitely less vulnerable to counterfeit fraud than magnetic stripe cards. The EMV standard continuously evolves to include new security defence mechanisms, such . Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
rfid tags for fixed assets
rfid credit card reviews
rfid tags for cattle in india
Explore the security of RFID card, the associated risks, and effective protection strategies. Learn how encryption, authentication, and physical barriers like RFID-blocking sleeves can safeguard your information. Learn what RFID technology is, how it works for identity verification, and how RFID verification is used at Regula. RFID chips are also used in credit cards with contactless payments. When you tap a credit card to pay for something, the machine reads an RFID chip embedded in the card. They’re also used for transit systems, tolls, and security access cards. They can be read by a machine with a quick tap. Many household pets also have RFID chips embedded in . Fortunately, theft with RFID cards is low due to built-in protections, which means that RFID cards are considered just as safe as the new EMV chips found in some debit and credit cards.
RFID credit cards are considered safe to use, and credit card fraud using RFID readers is rare and difficult to do. Radio-frequency identification (RFID) credit cards have a type of.
No, you shouldn't panic and start smashing your RFID-enabled credit cards and passports with a hammer. RFID is one of the many ways technology makes life more convenient but can lead to new security and privacy problems. RFID cards many times contain a facility code or other specific identifiers that cannot be quickly guessed. If an attacker captures that data from a known-valid card, the final identifier of another employee’s RFID credentials can .How Do RFID Blocking Cards Work - 2021 Guide. RFID security is a new way of ensuring personal information stored on electronics doesn’t end up in the wrong hands. Here’s how it works.
Since the chips are virtually impossible to tamper with or clone, EMV cards are infinitely less vulnerable to counterfeit fraud than magnetic stripe cards. The EMV standard continuously evolves to include new security defence mechanisms, such . Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
rfid credit card check
rfid tags for iphone
$34.20
rfid security cards validity|rfid verification process