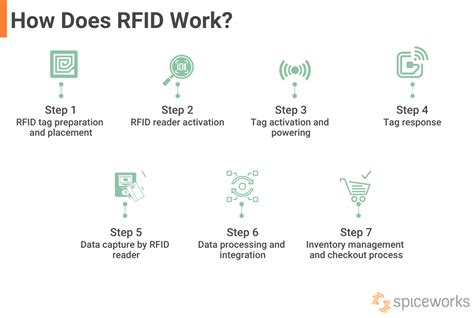
point of no return rfid chip The RFID chips are an important component of electronically-readable labels. The chips are EEPROMs (Electronically Erasable Programmable Read Only Memory), which can store their information without power over many years. This is how they work: The reader/scanner continuously transmits a radio signal that requests the RFID chip to register.
Try the phone App first to get the hang of it. Easier for testing and understanding the whole process. You create your record in the "Write" section, then you write your record, approach .
0 · what does rfid mean
1 · types of rfid chips
2 · rfid questions and answers
3 · rfid card information
4 · radio frequency rfid
5 · most common rfid questions
There are a couple of NFC readers that will be able to read unencrypted cards. I personally use "NFC Tools". But sadly afaik there is no way to emulate on a nonjailbroken iPhone, since .
eas rf system hard tag
there are several popular methods used in RFID tagging today: 1. NRZ (Non-Return to Zero) Direct. In this method no data encoding is done at all; the 1’s and 0’s are clocked from the data array directly to the output transistor. A low in the peak-detected modulation is a ‘0’ and a high .Products with RF-based dual technology labels are loss prevention-ready right off the delivery .
The RFID chips are an important component of electronically-readable labels. The chips are .there are several popular methods used in RFID tagging today: 1. NRZ (Non-Return to Zero) Direct. In this method no data encoding is done at all; the 1’s and 0’s are clocked from the data array directly to the output transistor. A low in the peak-detected modulation is a ‘0’ and a high is a ‘1’. 2. Differential Biphase. Several .Products with RF-based dual technology labels are loss prevention-ready right off the delivery truck, so no time is wasted. Using data collected from the RFID chips, you'll get more accurate shrinkage figures to target your hard tagging efforts for more effective protection.The RFID chips are an important component of electronically-readable labels. The chips are EEPROMs (Electronically Erasable Programmable Read Only Memory), which can store their information without power over many years. This is how they work: The reader/scanner continuously transmits a radio signal that requests the RFID chip to register.
high quality rf super security tag
report the sensor’s reading to the RFID reader. Chips can also have a self-destruct, or “kill” feature. This is a special code that, when received by the chip, causes the chip to no longer respond to commands. For financial applications, the full capabilities of smart cards have been combined with the wireless proto-A basic RFID system consists of these components: A programmable RFID tag/inlay for storing item data consisting of: an RFID chip for data storage. an antenna to facilitate communication with the RFID chip. A reader/antenna system to interrogate the RFID inlay.The use of RFID technology in closed-loop systems is as strong as applications for tracking goods. In 2008, the amount of RFID chips used in various closed-loop, mass transit tickets and cards was about equal to those used in open- supply chain goods tracking. Where speed and control are critical, radio frequency identification (RFID) is a hot technology solution. “Many returns come back to Best Buy minus their cartons. We add a new RFID tag at the point of return,” Jordan explains. “For us, the real value is having a system to track a product while it is under our control.
An RFID chip also offers comparatively vast data storage capabilities, giving end users a new way to track and store different types of data for diverse market applications. In the health care industry, end users have reported a return on investment up to for every medication tracked with RFID tags. Even the grocery business, where razor-thinAbstract—In this paper, we describe the sensitivity and impedance measurement method for UHF RF identification (RFID) chips. The measurements are performed using an RFID tester (RFID reader with variable output power and frequency) and a vector network analyzer.
Radiofrequency identification (RFID) chip implantation is increasing in the context of the growing body hacking movement. RFID chips may be used for personal identification and for contactless payments and other secure transactions.there are several popular methods used in RFID tagging today: 1. NRZ (Non-Return to Zero) Direct. In this method no data encoding is done at all; the 1’s and 0’s are clocked from the data array directly to the output transistor. A low in the peak-detected modulation is a ‘0’ and a high is a ‘1’. 2. Differential Biphase. Several .Products with RF-based dual technology labels are loss prevention-ready right off the delivery truck, so no time is wasted. Using data collected from the RFID chips, you'll get more accurate shrinkage figures to target your hard tagging efforts for more effective protection.The RFID chips are an important component of electronically-readable labels. The chips are EEPROMs (Electronically Erasable Programmable Read Only Memory), which can store their information without power over many years. This is how they work: The reader/scanner continuously transmits a radio signal that requests the RFID chip to register.
report the sensor’s reading to the RFID reader. Chips can also have a self-destruct, or “kill” feature. This is a special code that, when received by the chip, causes the chip to no longer respond to commands. For financial applications, the full capabilities of smart cards have been combined with the wireless proto-A basic RFID system consists of these components: A programmable RFID tag/inlay for storing item data consisting of: an RFID chip for data storage. an antenna to facilitate communication with the RFID chip. A reader/antenna system to interrogate the RFID inlay.
The use of RFID technology in closed-loop systems is as strong as applications for tracking goods. In 2008, the amount of RFID chips used in various closed-loop, mass transit tickets and cards was about equal to those used in open- supply chain goods tracking.
Where speed and control are critical, radio frequency identification (RFID) is a hot technology solution. “Many returns come back to Best Buy minus their cartons. We add a new RFID tag at the point of return,” Jordan explains. “For us, the real value is having a system to track a product while it is under our control.An RFID chip also offers comparatively vast data storage capabilities, giving end users a new way to track and store different types of data for diverse market applications. In the health care industry, end users have reported a return on investment up to for every medication tracked with RFID tags. Even the grocery business, where razor-thinAbstract—In this paper, we describe the sensitivity and impedance measurement method for UHF RF identification (RFID) chips. The measurements are performed using an RFID tester (RFID reader with variable output power and frequency) and a vector network analyzer.
what does rfid mean
types of rfid chips
rfid questions and answers
Add the option to scan tags while screen is locked. Currently I need to unlock my .I am using whiztags NFC tags with Gear S2, they are working with my mobile .
point of no return rfid chip|radio frequency rfid