rfid chip problems You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the . 13. First of all you have to get permission in AndroidManifest.xml file for NFC. The permissions are: .
0 · rfid problems and solutions
1 · rfid privacy and security issues
2 · rfid myths and facts debunked
3 · rfid issues and concerns
4 · rfid is vulnerable to
5 · rfid disadvantages
6 · rfid advantages and disadvantages
7 · currents news on rfid
Write text records to your NFC tag. Write Text To NFC Tag
rfid problems and solutions
Discover the most common RFID problems and learn proven solutions to optimize your system’s performance. This comprehensive guide covers troubleshooting tips for signal interference, . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and . You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the .
Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and .
rfid privacy and security issues
rfid myths and facts debunked
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos . Here are six common factors that can negatively impact an RFID system’s performance. Interference from other radio-frequency (RF) emitting devices (RFI), such as .There are two ways it can cause difficulties – firstly, one system can block the signal from another and prevent correct data being transmitted and/or received; and secondly, the signal from one .
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed .
RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your .Discover the most common RFID problems and learn proven solutions to optimize your system’s performance. This comprehensive guide covers troubleshooting tips for signal interference, . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and .
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a . RFID systems are extremely reliable; some enterprises achieve a 99.9% system reliability on their RFID network, but what happens when an RFID system is performing .
trovan rfid reader
Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and .
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos .Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed . Six RFID Trends for 2021 and Beyond. According to a recent RFID market report, the global market for RFID tags, readers and software is expected to reach .7 billion this .There are two ways it can cause difficulties – firstly, one system can block the signal from another and prevent correct data being transmitted and/or received; and secondly, the signal from one .
RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your .Discover the most common RFID problems and learn proven solutions to optimize your system’s performance. This comprehensive guide covers troubleshooting tips for signal interference, .
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and . You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a . RFID systems are extremely reliable; some enterprises achieve a 99.9% system reliability on their RFID network, but what happens when an RFID system is performing .
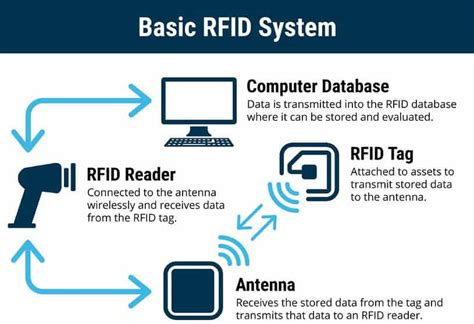
Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and .
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos .
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed . Six RFID Trends for 2021 and Beyond. According to a recent RFID market report, the global market for RFID tags, readers and software is expected to reach .7 billion this .
rfid issues and concerns
iPhone XR and above can automatically read and react when you hold an NFC tag near it. However, you’ll have to use the NFC Tag Reader from the Control Center for older devices.
rfid chip problems|rfid problems and solutions