smart card authentication method How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. How RFID/NFC Door Lock Works. The UIDs of authorized tags (key) are predefined in ESP32 code. When an RFID/NFC tag is tapped on RFID/NFC reader. ESP32 reads the UID from the reader. ESP32 compares the UID with .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
SEC Football Radio Online Broadcasts. Find SEC football radio online broadcasts and streaming audio for all fourteen schools. Find out where Alabama, Arkansas, Auburn, Florida, Georgia, Kentucky, LSU, Mississippi State, Missouri, Ole .
Microsoft Entra users can authenticate using X.509 certificates on their smart .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Microsoft Entra users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID at Windows sign-in. There's no special configuration needed on the Windows client to accept the smart card authentication. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication:
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
How Smart Card Authentication Works. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
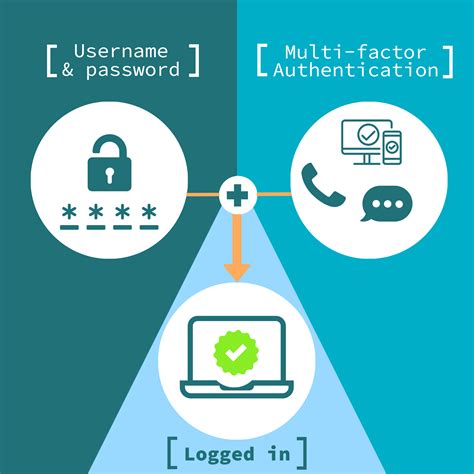
Smart card authentication works in combination with other components such as cryptographic tokens, security keys, personal identification numbers (PINs), and biometrics to provide a robust confirmation of a user's identity. Password-based authentication is the most common and simplest method of authentication for securing your network monitoring program. Here, the "password" might be a username-password combination, passcode, or PIN. It's intuitive, as many users are already familiar with such login methods.
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server. There are three common factors used for authentication: Something you know (such as a password) Something you have (such as a smart card) Something you are (such as a fingerprint or other biometric method) Identification occurs when a user professes an identity (such as with a username), and authentication occurs when users prove their identity.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
Microsoft Entra users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID at Windows sign-in. There's no special configuration needed on the Windows client to accept the smart card authentication. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify. Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication:
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. How Smart Card Authentication Works. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart card authentication works in combination with other components such as cryptographic tokens, security keys, personal identification numbers (PINs), and biometrics to provide a robust confirmation of a user's identity.
Password-based authentication is the most common and simplest method of authentication for securing your network monitoring program. Here, the "password" might be a username-password combination, passcode, or PIN. It's intuitive, as many users are already familiar with such login methods.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
auburn tiger radio
TIGER TALK. Thursdays at 6 p.m. CT. Hosted by Brad Law and the Voice of .
smart card authentication method|enable smart card authentication