f5 irule for smart card At this point, we have successfully configured a delegation account in Active Directory, configured APM to support smart card authentication as well as configure our OWA . MessageBox.Show("some other than timeout exception thrown while reading serial port"); } } } //end of CaptureWeight() One thing to note about my application is that I start the thread .
0 · f5 authentication requirements
1 · f5 authentication
$35.96
f5 authentication requirements
nfc tag not working iphone
F5 iRules have complete access to the x509 properties of a client certificate during that authentication and can look at the attribute of the certificate to make decisions. At this point, we have successfully configured a delegation account in Active Directory, configured APM to support smart card authentication as well as configure our OWA . iRules can route, re-route, redirect, inspect, modify, delay, discard or reject, log or . do just about anything else with network traffic passing through a BIG-IP. The idea behind . At this point, we have successfully configured a delegation account in Active Directory, configured APM to support smart card authentication as well as configure our OWA .
F5 iRules have complete access to the x509 properties of a client certificate during that authentication and can look at the attribute of the certificate to make decisions.
F5 iRules® scripting language is a patented F5 “network programming” environment. Based on industry standard Tool Control Language (TCL), iRules provide a simple, event-driven, . Thanks to a few very bright engineers on the F5 side who have implemented this solution before, my team was finally able to get this working. This article is solely around smart . iRules can route, re-route, redirect, inspect, modify, delay, discard or reject, log or . do just about anything else with network traffic passing through a BIG-IP. The idea behind .Your company uses smart cards for two-factor authentication. Users access different resources from a single url and need to be given access to those resources based on the properties of a .
iRules is a BIG-IP feature which plays a critical role in advancing the flexibility of the BIG-IP system. iRules can be written to make load balancing decisions, persisting, redirecting, .
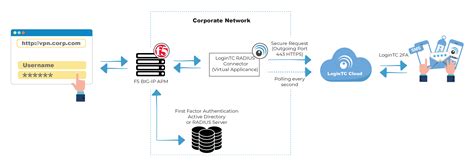
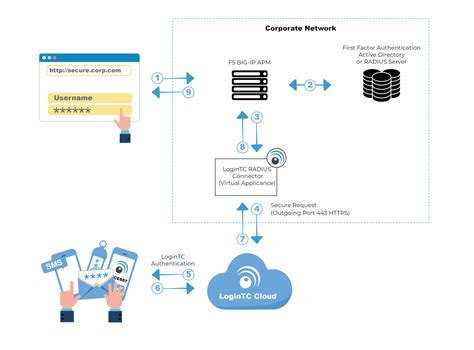
An iRule is a script that you write if you want individual connections to target a pool other than the default pool defined for a virtual server. iRules allow you to more directly specify the .You can use the BIG-IQ Local Traffic interface to attach iRules to a set of virtual servers. Adding an iRule sequence to a group of servers all at once can save time and help you cut down on .Supporting smart card PKI and federated access without exorbitant costs and additional tiers of infrastructure can now be achieved by leveraging a constrained delegation model and .
f5 authentication
At this point, we have successfully configured a delegation account in Active Directory, configured APM to support smart card authentication as well as configure our OWA .F5 iRules have complete access to the x509 properties of a client certificate during that authentication and can look at the attribute of the certificate to make decisions.F5 iRules® scripting language is a patented F5 “network programming” environment. Based on industry standard Tool Control Language (TCL), iRules provide a simple, event-driven, . Thanks to a few very bright engineers on the F5 side who have implemented this solution before, my team was finally able to get this working. This article is solely around smart .
iRules can route, re-route, redirect, inspect, modify, delay, discard or reject, log or . do just about anything else with network traffic passing through a BIG-IP. The idea behind .
Your company uses smart cards for two-factor authentication. Users access different resources from a single url and need to be given access to those resources based on the properties of a . iRules is a BIG-IP feature which plays a critical role in advancing the flexibility of the BIG-IP system. iRules can be written to make load balancing decisions, persisting, redirecting, .
An iRule is a script that you write if you want individual connections to target a pool other than the default pool defined for a virtual server. iRules allow you to more directly specify the .You can use the BIG-IQ Local Traffic interface to attach iRules to a set of virtual servers. Adding an iRule sequence to a group of servers all at once can save time and help you cut down on .
$899.00
f5 irule for smart card|f5 authentication requirements