smart card private key Feature description. Practical applications. Hardware requirements. Warning. . $179.95
0 · Virtual Smart Card Overview
1 · Transferring Your Private Key(s) To A Smartcard (Yubikey)
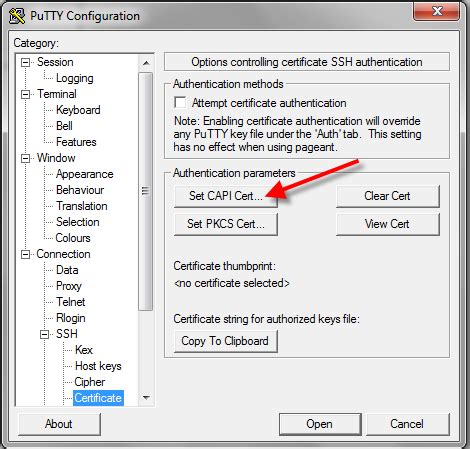
2 · Smart Card Logon for SSH
3 · Smart Card Group Policy and Registry Settings
4 · Smart Card Architecture
5 · Everything you need to know about Certificate
6 · Chapter 1. Understanding smart card authentication
13. First of all you have to get permission in AndroidManifest.xml file for NFC. The permissions are: . More -> and enable it. NFC tags costs from $1 to $2. In manifest.xml, add the following. The uses-permission and uses-feature tags .
In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key. The TLS-related private key operation occurs on the smart card, and the user is .
Transferring, or importing, the private onto the Smartcard is a bit easier than .Your PIV/CAC credential contains an authentication certificate key pair (public and private) for .
Feature description. Practical applications. Hardware requirements. Warning. . This article for IT professionals and smart card developers describes the Group .
In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key. The TLS-related private key operation occurs on the smart card, and the user is authenticated and signed in; The user returns to Outlook to send another signed e-mail. This time, the user isn't prompted for a PIN because the PIN is cached from the previous operation.
Transferring, or importing, the private onto the Smartcard is a bit easier than importing PIV certificates. You can use the usual gpg tools. gpg --card-status
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH. Feature description. Practical applications. Hardware requirements. Warning. Windows Hello for Business and FIDO2 security keys are modern, two-factor authentication methods for Windows. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. This article for IT professionals and smart card developers describes the Group Policy settings, registry key settings, local security policy settings, and credential delegation policy settings that are available for configuring smart cards.You can store user credentials on a smart card in the form of a private key and a certificate, and special software and hardware is used to access them. Place the smart card into a reader or a USB port and supply the PIN code for the smart card instead of providing your password.
What benefits do smart cards capable of storing private keys, and devices like the YubiKey Neo (which seems to be a smart card + usb reader in a single dongle) offer above storing private keys on a plain-old usb thumb drive? Does the smart card ever "reveal" the private key to applications like SSH or GPG?
how to mimic an rfid badge with your phone
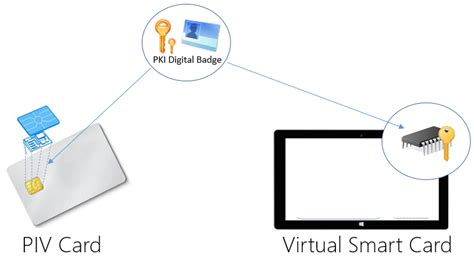
Virtual Smart Card Overview
 To A Smartcard (Yubikey).jpg)
7. The Relation of Smart Cards with PKI. As we already know smart cards are secure place to hold sensitive data, such as money and identity. And if the identity is the subject we should talk about PKI, Public Key Infrastructure, and smart cards. Think that, you are working in a company with many branch offices and many facilities. Using a smart card can keep your private keys safe even if your computer is compromised. Just make sure you do some research on your reader and the card you are looking to buy to make sure it will work with your OS / application.
In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key. The TLS-related private key operation occurs on the smart card, and the user is authenticated and signed in; The user returns to Outlook to send another signed e-mail. This time, the user isn't prompted for a PIN because the PIN is cached from the previous operation. Transferring, or importing, the private onto the Smartcard is a bit easier than importing PIV certificates. You can use the usual gpg tools. gpg --card-status
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.
Feature description. Practical applications. Hardware requirements. Warning. Windows Hello for Business and FIDO2 security keys are modern, two-factor authentication methods for Windows. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. This article for IT professionals and smart card developers describes the Group Policy settings, registry key settings, local security policy settings, and credential delegation policy settings that are available for configuring smart cards.You can store user credentials on a smart card in the form of a private key and a certificate, and special software and hardware is used to access them. Place the smart card into a reader or a USB port and supply the PIN code for the smart card instead of providing your password.
What benefits do smart cards capable of storing private keys, and devices like the YubiKey Neo (which seems to be a smart card + usb reader in a single dongle) offer above storing private keys on a plain-old usb thumb drive? Does the smart card ever "reveal" the private key to applications like SSH or GPG?7. The Relation of Smart Cards with PKI. As we already know smart cards are secure place to hold sensitive data, such as money and identity. And if the identity is the subject we should talk about PKI, Public Key Infrastructure, and smart cards. Think that, you are working in a company with many branch offices and many facilities.
Transferring Your Private Key(s) To A Smartcard (Yubikey)
how to make smart phone rfid card
O3DS don't have the amiibo reader built in like on the N3DS so you need to buy the accessory .
smart card private key|Transferring Your Private Key(s) To A Smartcard (Yubikey)